GE-625 / 635
Programming
Reference Manual

GE-625 / 635
Programming
Reference Manual

GE-625/635
PROGRAMMING
REFERENCE MANUAL
July 1964
Rev. January 1966
GENERAL  ELECTRIC
ELECTRIC
COMPUTER DEPARTMENT
The GE-625/635 Programming Reference Manual is the basic document for programming the GE-625/635. It essentially describes programming-related GE-625/635 machine features, the instruction repertoire, and the symbolic machine language oriented Macro Assembler. The Assembler chapter and the examples in Chapter IV describe how the programmer may write Processor instructions using a symbolic notation.
The Programming Reference Manual is one of a set of user publications
for programming the GE-625/635 computer. The others of the set, together
with pertinent and necessary programming information contained in each,
are:
| PUBLICATION | PROGRAMMING INFORMATION |
|---|---|
| GE-625/635 FORTRAN IV
Reference Manual, CPB-1006 | FORTRAN IV language specifications, coding rules and restrictions,
and compiler informa-tion for the GE-625/635
|
| GE-625/635 COBOL
Reference Manual, CPB.-1007 | COBOL-61 Extended language specifications, coding rules and
restrictions and compiler information for the GE-625/635
|
| GE-625/635 File and Record Control Reference Manual, CPB-1003 (GE FRC) | Standard input/output coding by use of calling sequences to
software system input/output routines.
|
| GE-625/635 Comprehensive Operating Supervisor Reference Manual, CPB-1002 (GE COS) |
|
| GE-625/635 General Loader Reference Manual, CPB-1008, (GE LOAD) |
|
| GE-625/635 Sort/Merge Reference Manual, CPB-1005 |
|
| GE-625/ 635 Bulk Media Conversion Reference Manual, CFB-1096 | Description of deck preparation for bulk media conversion run |
This reference manual is addressed to programmers experienced with coding in the environment of a large-scale computer installation. It assumes some knowledge and experience in the use of address modification with indirection, hardware indicators, fault interrupts and recovery routines, macro operations, pseudo-operations, and other features normally encountered in a fast, large memory capacity computer with a very flexible instruction repertoire - -under control of a master executive program. It is also assumed that the programmer is familiar with the 2's complement number system as used in a sign-number machine.
Comments on this publication niay be addressed to Technical Publications,
Computer Department, General Electric Company, P. 0. Box 2961, Phoenix,
Arizona, 85002.
 |
 |
| Figure | Page | |
|---|---|---|
| II-1 | Block Diagram of Principal Processor Registers | |
| II-2 | Table of Faults | |
| II-3 | Ranges of Fixed-Point Numbers | |
| II-4 | Ranges of Floating-Point Numbers | |
| II-5A | Address Modification Flow Chart | |
| II-5B | Address Modification Flow Chart | |
| III-1 | GE-625/635 MacroAssembler coding Form |
 |
The basic GE-625/635 computer system is made up of four principle hardware components:
The Memory module, unlike most computer systems which are processor-oriented, is the over-all system control agency. It serves as a passive coordinating component that provides interim information storage and general system communication control. The module comprises two major functional units: the System Controller and the Magnetic Core Storage Unit. The principle features of the module and the performing units are:
| FEATURE | FUNCTIONAL UNIT | ||||||||
|---|---|---|---|---|---|---|---|---|---|
| System Controller (eight priority-linked channel cells plus an associated mask register) | ||||||||
|
The Processor module is composed of two principal functional units: the Program Control Unit and the Operations Unit. The chief features of the module and the performing units are:
|
The Input/Output Controller module is the coordinator of all input/output data transfers between the complement of peripheral subsystems and the Memory module. It is in fact a separate processor which, when provided with certain required information from the Comprehensive Operating Supervisor and the user program, works independently of the Processor module under control of its own permanently-wired program.
The major functional units of the Input Output Controller are (1) the Memory Interface, (2) the Buffer Storage, (3) the Micro-Program Generator, (4) the I-O Processor, and (5) the PUB* Interrupt Service. The main features of this module and the performing units are:
| FEATURE | FUNCTIONAL UNIT | ||||||
|---|---|---|---|---|---|---|---|
|
 |
The primary objectives of the GE-635 software system are:
The attainment of these objectives is achieved by the General Comprehensive Operating Supervisor (GECOS) (the overall manager of the software system) through efficient use of the hardware features and the supervision of a multiprogramming environment (which is the normal operating mode of the GE-625/635). The significant features provided by the Operating Supervisor as related to the several primary objectives above are summarized in the list following. These features are implemented by the modules and submodules within the Comprehensive Operating Supervisor.
Although each user-programmer writes his job program as though he had exclusive use of the computer, he is in fact generating a program that will reside concurrently in memory with other user programs and will be executed in a time-shared manner; that is, any given program is processed until it is held up (usually because of the need for some input/output to be completed) at which time the next most urgent program is processed. Transfer between programs under multiprogram execution is performed by means of the hardware interrupt facility (in the System Controller) working with the Dispatcher routines in the Input/Output Supervisor. The ways by which a user program can be temporarily delayed in execution are:
| DELAY TYPE | REASON |
|---|---|
| Roadblock | Program cannot progress until all input/output requests have terminated |
| Relinquish | Program relinquishes control so that some other program may be executed |
| Forced Relinquish | Program was interrupted because a timer run-out occurred. |
Each time a program yields control to the Operating Supervisor by means of Roadblock, Relinquish or by Forced Relinquish listed above, the Supervisor has the opportunity to give control to another program in core which can make effective use of the Processor.
In giving such control, the Supervisor examines the following conditions:
Media conversions are of two basic types (1) bulk media conversion, whereby large volumes of data in a single format and for a single purpose are processed and, (2) system media con-version where low-volume sets of data--each with its own format and purpose--are processed.
Bulk media conversion is performed by a system routine which may be called into execution by use of a control card. Other control cards will direct the routine as to where to find the input and where to place the output.
On-line media conversions for both input and output are performed as a normal part of the multiprogramming environment of the GE-625/635, Normal job input is carried out by input media conversion, which reads card input from the card reader, scans the control cards for execution information, and records the job on the input queue located on the system drum.
System media conversions of program output data are automatically
performed by the Output Media Conversion routine executed in protected
memory. The programmer specifies that a particular output file be written
on the permanently assigned system output (SYSOUT) file by use of the
PRINT, PUNCH, or WTREC calling sequences described in the GE-635 File
and Record Control Reference Manual. Once on the SYSOUT file, the output
is converted to hard copy or punched cards by the Output Media Conversion
routine, concurrently with other user programs under execution in the
multiprogramming environment.
Centralized Input/Output
In the multiprogramming environment where several programs may concurrently request input/ output, a facility must be provided (1) for processing such multiple requests in terms of the efficient use of the entire peripheral complement and, (2) for maintaining continuous processing of the multiple programs in core storage. The Comprehensive Operating Supervisor module that performs these general functions is the Input/Output Supervisor.
The main functions of the Input/Output Supervisor are to initiate an input/output activity and to respond to the termination of an input/output activity. In addition, the Input/Output Super-visor provides the following functions:
When the Input/Output Supervisor receives a request to perform an input/output function, it looks at the communication cells and issues a connect instruction. If the particular channel is busy, the request is placed in a waiting queue. If the request queue is full or if the program indicated that it should be roadblocked until all input/output is complete, then control is given to another program residing in memory.
When the input/output operation terminates, control is given to the
Input/Output Supervisor to perform all necessary termination functions.
At this point, the request queue is examined and if any requests for
the channel are in queue, they will be executed.
Master/Slave Relationship
Each Processor has the capability of operating in the Slave Mode or in the Master Mode. Master Mode is established for exclusive use by the Operating Supervisor. When executing a user program. a Processor is in Slave Mode. The prime reason for the Master Mode of operation is to protect the Operating Supervisor and user programs as well from modification by other user programs. This feature is vital in the multiprogramming environment and is closely tied in with memory protection, accounting determinations, multiprogram interrupt management, intermodule communications control, and input/output operations. Each of these functions is implemented by a Processor instruction that requires the Master Mode. These are listed below.
All instructions available to the Processor in Slave Mode are available in Master Mode. The following instructions can be executed only when the Processor is in Master Mode.
The last of these instructions, Connect Input/Output Channel, is the
beginning of every peripheral operation. Thus, all peripheral operations
are reserved for execution in Master Mode, and in particular by the
Input/Output Supervisor within the Comprehensive Operating Supervisor.
Master Mode Entry
Although Master Mode operation by the Processor is a primary safeguard
for executive routines and user programs in memory, the applications
programmer can force the Processor into this mode but only for accessing
routines that are part of the Operating Supervisor. This is done by use
of the Master Mode Entry (MME) instruction and one of the system-symbol
operands listed in Appendix E and described fully in the General
Comprehensive Operating Supervisor Manual. Any other use of MME causes
an abort of the user program. Thus, through the MME instruction, the
programmer can communicate with modules of the Operating Supervisor to
exchange any necessary information for the execution of his program.
Mass Storage Orientation
"Compute overhead" time is reduced and multiprogramming is enhanced through the use of an external drum (mass) storage unit. The drum (and optionally a disc storage device) enables optimized accessing of system routines and performs data transfers at higher rates than other external storage media.
The drum and or disc is used primarily for the following purposes:
The software system is further described as file oriented because
(1) the Comprehensive Opera-ting Supervisor assigns peripheral devices
to an activity and (2) it manages all assigned periph-erals during input
or output operations so that the programmer never deals directly with
input/ output subsystems or devices. The programmer references all
peripherals by use of file code designators, two alphanumeric characters,
that are referenced in two ways: (1) on file control cards used by the
Allocator in the Operating Supervisor to specify those files needed to
execute
the activity and, (2) in communicating to the File and Record Control
program or to the Input/Output Supervisor. The file code designators and
their assigned peripheral devices are maintained in the Peripheral
Assignment Table (PAT) used by the Input/Output Supervisor for
peripheral identification.
Software Reference Documentation
The following manuals and documents contain detailed descriptions of items mentioned in this chapter.
 |
Since the Control Unit runs independently of the Memory module, a single Processor can be connected to memories with different cycle times. The Processor is designed to eliminate adverse interaction when memories with different cycle times are employed.
The Operations Unit performs all arithmetic and logical operations as directed by the Control Unit. The Operations Unit contains most of the registers available to a user program. This unit performs such functions as:
To permit separation of control and object programs with corresponding protection of control programs from undebugged object programs, two modes of operation, Master and Slave, are provided in the Processor. Control programs will run in the Master Mode, and object programs will run in the Slave Mode. Programs running in Master Mode have access to the entire memory, may initiate peripheral and internal control functions, and do not have base address relocation applied. Programs running in Slave Mode have access to a limited portion of the memory, cannot generate peripheral control functions, and have the Base Address Register added to all relative memory addresses of the object program.
Master Mode operation is the state in which the Processor:
The Processor is in the Master Mode when any of the following exists:
Slave Mode operation is the state in which the Processor:
The Processor is in the Slave Mode when the Master Mode Indicator is in
the slave condition or when the Transfer and Set Slave (TSS) instruction
is being executed. (See page II- 11.)
Operation Overlapping
Instruction words are fetched in pairs and sequentially transferred to the Control Unit of the Processor where the instructions are directed to the primary and secondary instruction registers of the instruction decoder. If required, address modification is then performed using the first of the two instructions.
As soon as this is accomplished, the operand specified by the first instruction is requested from memory while the Control Unit concurrently performs any address modification required by the second of the instruction pair.
When the operand called for by the first instruction is obtained, the
Control Unit transfers the operand to the Operations Unit, thus initiating
the specified operation to be carried out. While this operation is being
carried out by the Operations Unit, the operand specified by the second
instruction is requested by the Control Unit. As soon as the second operand
is received and the Operations Unit has finished with the first operand,
the Control Unit signals the Oprations Unit to carry out the second operation.
Finally, while the second operation is being carried out, the next instruction
pair is requested from memory.
Address Range Protection
Any object program address to be used in a memory access request while the Processor is in the Slave Mode is checked, just prior to the fetch, for being within the address range allocated by the Comprehensive Operating Supervisor (GECOS) to the program for this execution. This address range protection is commonly referred to as memory protection.
For the purpose of memory protection, the 18-bit Processor Base Address Register is loaded by GECOS with an address range in bit positions 9-16. The check takes place only in the Slave Mode. It consists of subtracting bit positions 0-7 of the program address from this address range, using the boundary adder. When the result is zero or negative, then the program address is out of range; and a Memory Fault Trap occurs. (Refer to page 11-14.)
More specifically, the checking is actually based on nine bits, namely the Base Address Register positions 9-17 and the bit positions 0-8 of the program address. This permits address range allocation to job programs in multiples of 512 words. Because of a software requirement, bits 8 and 17 of the Base Address Register have been wired in such a way that they contain zeros permanently and cannot be altered by the LBAR instruction. Thus, memory allocation and protection is performed in multiples of 1024 words.
In the Master Mode no checking takes place; thus, any memory location (in
those Memory modules that are connected to this Processor) can be accessed.
Execution of Interrupts
When an execute interrupt request present signal is received from a Memory module system controller for which the Processor is the control Processor, the Processor carries out the interrupt procedure as soon as an instruction from an odd memory location has been executed that:
The interrupt procedure consists of the following steps:
-------------+--------+-----------+---+------------------------- | 000 000 000 | Memory | Interrupt | 0 | Operation code, inhibit | | | No | Cell No. | | bit and tag fields | -------------+--------+-----------+---+------------------------- 0 8 9 11 12 16 17 18 35
The memory number is determined by the position of the address reassignment switches (A0 A1 A2 ) associated with the system controller causing the execute interrupt. The switches are three-position toggles having the positions 0, 1, and EITHER. A switch in the EITHER position is interpreted as a 0 in preparing the address for the instruction.
The cell number is determined by the highest priority unmasked interrupt cell (in the system controller) causing the execute interrupt.
Each of the two instructions from the memory location Y-pair may affect the Master Mode Indicator as follows:
The first of the two instructions from the memory location Y must not
alter the contents of the location of the second instruction, and must
not be an XED instruction. If the first of the two instructions alters
the contents of the Instruction Counter, then this transfer of control
is effective immediately; and the second of the two instructions is
not executed.
Interval Timer
The Processor contains a timer which provides a program interrupt at
the end of a variable interval. The timer is loaded by GECOS and can be
set to a maximum of approximately four minutes total elapsed time.
(See pages 11-7 and 11-13)
REGISTERS
The Processor block diagram (Figure lI-i) shows the program accessible registers as well as the major nonprogram accessible registers, adders, and switches. Only data and information paths are shown. The block diagram also shows the division between the Operations Unit and Control Unit.
The switches (rounded figures on the block diagram) control the flow of
information between the registers, adders, and the memory interface.
Program Accessible Registers
The following table shows the registers accessible to the program.
| Name | Mnemonic | Length |
|---|---|---|
| Accumulator Register | AQ | 72 bits |
| Eight Index Registers (n=O,. 3) | Xn | 18 bits each |
| Exponent Register | B | 8 bits |
| Base Address Register | BAR | 18 bits |
| Indicator Register | IR | 18 bits |
| Timer Register | TR | 24 bits |
| Instruction Counter | IC | 18 bits |
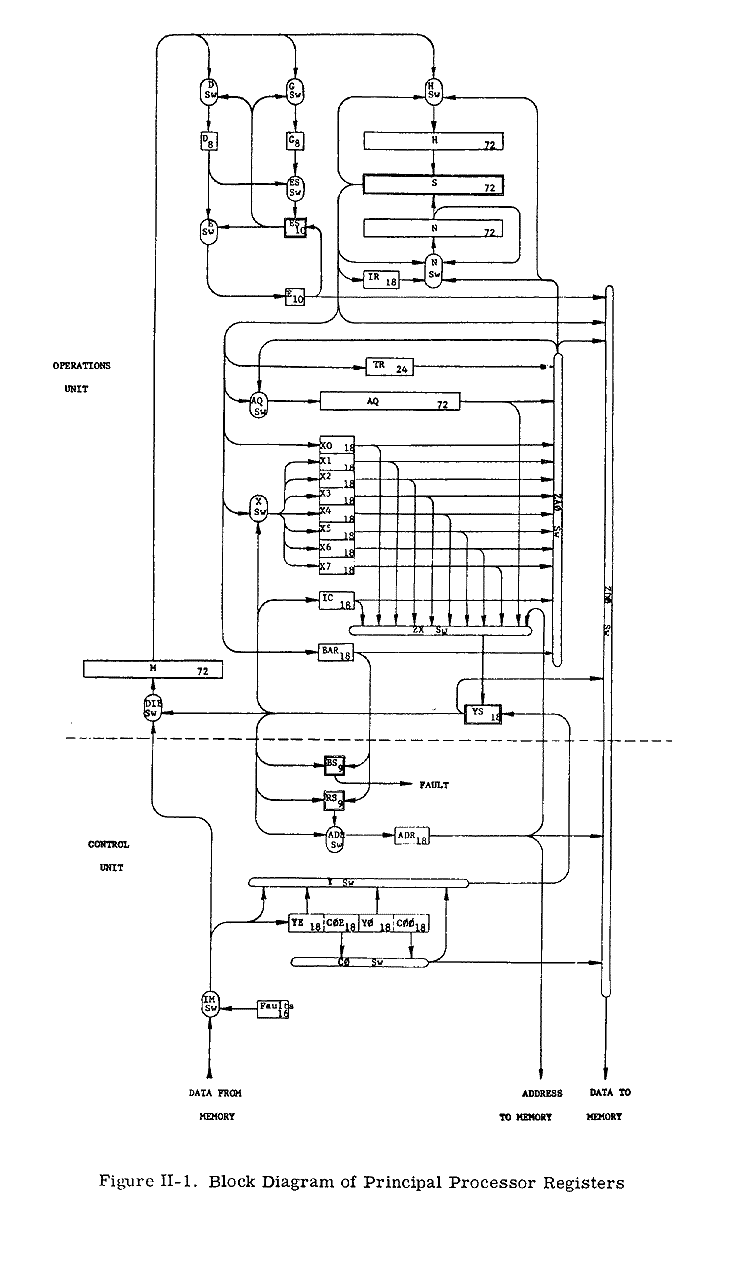
Program Nonaccessible Registers
The following listed registers are used in Processor operations but are not referenced in machine instructions.
| Mnemonic | Length |
|---|---|
| M | 72 bits |
| H | 72 bits |
| N | 72 bits |
| D | 8 bits |
| G | 8 bits |
| ADR | 18 bits |
| YE | 18 bits |
| YO | 18 bits |
| COE | 18 bits |
| COO | 18 bits |
The following table lists the Processor adders.
| Name | Length |
|---|---|
| S | 72 bits |
| YS | 18 bits |
| ES | 10 bits |
| BS | 9 bits |
| RS | 9 bits |
The indicators can be regarded as individual bit positions in an 18-bit half-word Indicator Register (IR).
An indicator is set to the ON or OFF state by certain events in the Processor, or by certain instructions. The ON state corresponds to a binary 1 in the respective bit position of the IR; the OFF state corresponds to a 0.
The description of each machine instruction on pages II-39 through II-137 includes a statement about (1) those indicators that may be affected by the instruction and (2) the condition under which a setting of the indicators to a specific state occurs. If the conditions stated are not satisfied, the status of this indicator remains unchanged.
The instruction set includes certain instruction which transfer data between the lower half of a storage location and the Indicator Register. The following table lists the indicators that have been implemented, their relation to the bit positions of the lower half of a memory location, and the instructions directly affecting indicators.
| Assigned | Bit Position | Indicator | Indicator Instructions | ||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Assigned | 18 | Zero |
|
The following descriptions of the individual indicators are limited to
general statements only.
Zero Indicator
The Zero Indicator is affected by instructions that change the contents
of a Processor register (A, Q, AQ, Xn, BAR, IR, TR) or adder, and by
comparison instructions.
The indicator is set ON when the new contents of the affected register
or adder contains all binary 0's; otherwise the indicator is set OFF.
Negative Indicator
The Negative Indicator is affected by instructions that change the contents of a Processor register (A, Q, AQ, Xn, BAR, IR, TR) or adder, and by comparison instructions.
The indicator is set ON when the new contents of bit position 0 of this
register or adder is a binary 1; otherwise it is set OFF.
Carry Indicator
The Carry Indicator is affected by left shifts, additions, subtractions, and comparisons.
The indicator is set ON when a carry is generated out of bit position
0; otherwise it is set OFF.
Overflow Indicator
The Overflow Indicator is affected by the arithmetic instructions,
but not by compare instructions and Add Logical (ADL(R)) or Subtract
Logical (SBL(R)) instructions
Exponent Overflow Indicator
The Exponent Overflow Indicator is affected by arithmetic operations with floating-point numbers or with the exponent register (E).
The indicator is set ON when the exponent of the result is larger than +127 which is the upper limit of the exponent range.
Since it is not automatically set to OFF otherwise, the Exponent
Overflow Indicator reports any exponent overflow that has happened since
it was last set OFF by certain instructions
(LDI, RET, and
Transfer on Exponent Overflow (TEO)).
Exponent Underflow Indicator
The Exponent Underflow Indicator is affected by arithmetic operations with floating-point numbers, or with the exponent register (E).
The indicator is set ON when the exponent of the result is smaller than -128 which is the lower limit of the exponent range.
Since it is not automatically set to OFF otherwise, the Exponent
Underfiow Indicator reports any exponent underflow that has happened
since it was last set OFF by certain instructions
(LDI, RET, and
Transfer on Exponent Underflow (TEU)).
Overflow Mask Indicator
The Overflow Mask Indicator can be set ON or OFF only by the instructions LDI and RET.
When the Overflow Mask Indicator is ON, then the setting ON of the Overflow Indicator, Exponent Overflow Indicator, or Exponent Underflow Indicator does not cause an Overflow Fault Trap to occur. When the Overflow Mask Indicator is OFF, such a trap will occur.
Clearing of the Overflow Mask Indicator to the unmask state does not
generate a fault from a previously set Overflow Indicator,
Exponent Overflow Indicator, or Exponent Underfiow Indicator.
The status of the Overflow Mask Indicator does not affect the setting,
testing, or storing of the Overflow Indicator, Exponent Overflow Indicator,
or Exponent Underflow Indicator.
Tally Runout Indicator
The Tally Runout Indicator is affected by the Indirect Then Tally (IT) address modification type (all designators except Indirect and Fault) and by the Repeat, Repeat Double, and Repeat Link instructions (RPT, RPD, and RPL).
The termination of a Repeat instruction because a specified termination condition is met sets the Tally Runout Indicator to OFF.
The termination of a Repeat instruction because the tally count reaches
0 (and for RPL because of a 0 link address) sets the Tally Runout Indicator
to ON; the same is true for tally equal to 0 in some of the IT address
modifications.
Parity Error Indicator
The Parity Error Indicator is set to ON when a parity error is detected during the access of one or both words of Y-pair from memory.
It may be set to OFF by the LDI or
RET instruction.
Parity Mask Indicator
The Parity Mask Indicator can be set to ON or OFF only by the instructions
LDI and RET.
When the Parity Mask Indicator is ON, the setting of the Parity Error
Indicator does not cause a Parity Error Fault Trap to occur. When the
Parity Mask Indicator is OFF, such a trap will occur.
Clearing of the Parity Mask Indicator to the unmasked state does not
generate a fault from a previously set Parity Error Indicator. The status
of the Parity Mask Indicator does not affect the setting, testing, or
storing of the Parity Error Indicator.
Master Mode Indicator
The Master Mode Indicator can be changed only by an instruction. For a description of how the indicator can be changed, refer to the following instruction descriptions:
| Instruction | Reference |
|---|---|
| Master Mode Entry (MVIE) | Page II-123 |
| Return (RET) | Page II-116 |
| Derail (DRL) | Page II-124 |
| Transfer and Set Slave (TSS) | Page II-115 |
When the Master Mode Indicator is ON, the Processor is in the Master
mode; however, the converse is not necessarily true. (See the MME and
DRL descriptions.)
FAULT TRAPS
Trapping Procedure
Sixteen types of faults and other events each have a fault trap assigned. Some of these events have nothing to do with actual faults; they are included here because they are treated the same as faults.
The fault trap procedure is similar to the interrupt procedure (page II-4) except that the effective address is defined differently. The fault trap procedure consists of the following steps:
-------+------------+------------+--- | ZEROS | Constant | Code | 0 | -------+------------+------------+--- 0 5 6 12 13 16 17
Each of the two instructions from the memory location Y-pair may affect the Master Mode Indicator as follows: If this instruction results in an actual transfer of control and is not the Transfer and Set Slave instruction (TSS), then ON: if this instruction is either the Return instruction (RET) with bit 28 equal to 0 or the TSS instruction, then OFF.
The first of the two instructions from the memory location Y must not
alter the contents of the location of the second instruction, and must not
be an Execute Double instruction (XED). If the first of the two
instructions alters the contents of the Instruction Counter, then this
transfer of control is effective immediately; and the second of the two
instructions is not executedú
Fault Categories
There are four general categories of faults:
If a parity error occurs on any instruction for which the C(Y) are taken from a location (this includes "to storage" instructions, ASA, ANSA, etc., the Processor operation is completed with the faulty operand before entering the fault routine.
The generation of this fault is inhibited when the Parity Mask Indicator is in the mask state. Subsequent clearing of the Parity Mask to the unmasked state will not generate this fault from a previously set Parity Error Indicator. The Parity Mask does not effect the setting, testing, or storing of the Parity Indicator.
The above two are dependent on other switch positions on the Processor control panel.
The 16 faults are organized into five groups to establish priority for the recognition of a specific fault when faults occur in more than one group. Group I has highest priority.
Only one fault within a priority is allowed to be active at any one
time. In the event that two or more faults occur concurrently, only the
fault which occurs first through normal program sequence is permitted.
Fault Recognition
Faults in Groups I and II cause the operations in the Processor to abort unconditionally.
Faults in Groups III and IV cause the operations in the Processor to abort conditionally upon the completion of the operation presently being executed.
Faults in Group V are recognized under the same conditions that
Program Interrupts are recognized. (See page II-4.) Faults in Group V
have priority over Program Interrupts and are also subject to being
inhibited form recognition by use of the inhibit bit in the instruction
word.
Instruction Counter (IC)
Upon recognition of a fault, the contents of the Instruction Counter (IC) are shown in the Table of Faults below.
| Fault No. | Fault Name | Group (Priority) | IC Contents |
|---|---|---|---|
| 1100 | Startup | I | N+0,1, or 2 |
| 1111 | Execute | I | N+0,1, or 2 |
| 1011 | Operation Not Completed | II | N+0,1, or 2 |
| 0111 | Lockup | II | N+0,1, or 2 |
| 1110 | Divide Check | III | N (Note 4) |
| 1101 | Overflow | III | N |
| 1001 | Parity | IV | N (Note 2) |
| 0101 | Command | IV | N+1 |
| 0001 | Memory | IV | N+1 (Note 4) |
| 0010 | Master Mode Entry | IV | N (Note 4) |
| 0110 | Derail | IV | N (Note 4) |
| 0011 | Fault Tag | IV | N (Note 4) |
| 1010 | Illegal Op Code | IV | N |
| 1000 | Connect | V | N |
| 0100 | Timer Runout | V | N |
| 0000 | Shut Down | V | N |
Notes:
Figure II-2. Table of Faults
THE NUMBER SYSTEM
The binary system of notation is used throughout the GE-635 information processing system.
Many of the instructions, mainly additions, subtractions, and comparisons, can be used in two ways: either operands and results are regarded as signed binary numbers in the 2's complement form (the "arithmetic" case), or they are regarded as unsigned, positive binary numbers (the "logic" case). The Zero and the Negative Indicators facilitate the general interpretation of the results in the arithmetic case; the Zero and the Carry Indicators, in the logic case. The instruction set contains instruction types "Add Logic" and "Subtract Logic" which particularly facilitate arithmetic of the logic type with half-word, single-word, and double-word precision.
Subtractions are carried out internally by adding the 2's complement of the subtrahend.* It is a characteristic feature of the 2's complement representation that a "no borrow" condition in the case of true subtraction corresponds to a "carry" condition in the case of addition of the 2's complement, and vice versa.
A statement on the assumed location of the binary point has
significance only for multiplications and divisions. These two operations
are implemented for integer arithmetic as well as for fractional
arithmetic with numbers in 2's complement form, "integer" meaning that
the position of the binary point may be assumed to the right of the
least-significant bit position (that is, to the right of bit position
35 or 71, depending on the precision of the respective number) and
"fractional" meaning that the position of the binary point may be
assumed to the left of the most-significant bit position (that is,
between the bit positions 0 and 1).
REPRESENTATION OF INFORMATION
The Processor is fundamentally organized to deal with 36-bit groupings
of information. Special features are also included for ease in
manipulating 6-bit groups, 18-bit groups, and 72-bit, double-precision
groups. These bit groupings are used by the hardware and software to
represent a variety of forms of information.
Position Numbering
The numbering of bit positions, character positions, words, etc., increases in the direction of conventional reading and writing: from the most- to the least-significant digit of a number, and from left to right in conventional alphanumeric text.
Graphical presentations in this manual show registers and data with
position numbers increasing from left to right.
The Machine Word
The machine word consists of 36 bits arranged as follows:
0 17 | 18 35 ------------------+----------------- | One Machine Word | ------------------+----------------- Upper Half word | Lower Half word
Data transfers between the Processor and memory are word orientated: 36 bits are transferred at a time for single-precision data and two successive 36-bit word transfers for double-precision data. When words are transferred to a Magnetic Core Storage Unit, this unit adds a parity bit to each 36-bit word before storing it. When words are requested from a Magnetic Core Storage Unit, this unit verifies the parity bit read from the store and removes it from the word transferred prior to sending each word to the Processor.
The Processor has many built-in features for transferring and processing pairs of words, transferring a pair of words to or from memory, a pair of memory locations is accessed; the addresses are an even and the next-higher odd number.
0 35 | 36 72 ------------------+----------------- | A Pair of Machine Words | ------------------+----------------- Even Address | Odd Address
In addressing such pairs of machine locations in an instruction that is intended for handling pairs of machine words, either of the two addresses may be used as the effective address (Y). Thus,
If Y is even, the pair of locations (Y, Y+1) is accessed. If Y is odd, the pair of locations (Y-1, Y) is accessed. The term "Y-pair" is used for each such pair of addresses.
Alphanumeric data are represented by six-bit or nine-bit characters. A machine word contains either six or four characters:
Character positions within a word :
------+------+------+------+------+------ | 0 | 1 | 2 | 3 | 4 | 5 | six-bit ------+------+------+------+------+------ 0 5 6 11 12 17 18 23 24 29 30 35 ---------+---------+---------+--------- | 0 | 1 | 2 | 3 | nine-bit ---------+---------+---------+--------- 0 8 9 17 18 26 27 35
-----+-----+-----+-----+-----+----- | 0 | 1 | 3 | 4 | 4 | 5 | six-bit -----+-----+-----+-----+-----+----- -----+-----+-----+-----+-----+-----+-----+-----+----- | 0 | 1 | 3 | 4 | 4 | 5 | 6 | 7 | 8 | nine-bit -----+-----+-----+-----+-----+-----+-----+-----+-----
The character set used is the Computer Department Standard Character
Set, which is readily convertible to and from the ASCII character set.
Binary Fixed-Point Numbers
The instruction set comprises instructions for binary fixed-point arithmetic with half-word, single-word, and double-word precision.
PRECISION REPRESENTATION
--------- --------------
------------------ - - - - - - - - -
Upper Half | | |
------------------ - - - - - - - - -
0 17
Half-word
- - - - - - - - - -----------------
Lower Half | | |
- - - - - - - - - -----------------
18 35
----------------------------------
Single-word | |
----------------------------------
0 35
---------------------------------- ----------------------------------
Double-word | | |
---------------------------------- ----------------------------------
0 35 36 72
Even Address Odd Address
Instructions can be divided into two groups according to the way in which the operand is interpreted: the "logic" group and the "algebraic" group.
For the "logic" group, operands and results are regarded as unsigned, positive binary numbers. In the case of addition and subtraction, the occurrence of any overflow is reflected by the carry out of the most-significant (leftmost) bit position:
| 1. | Addition | -- If the carry out of the leftmost bit position equals 1, then the result is above the range. |
| 2. | Subtraction | -- If the carry out of the leftmost bit position equals 0, then the result is below the range. |
In the case of comparisons, the Zero and Carry Indicators show the relation.
For the "algebraic" group, operands and results are regarded as signed, binary numbers, the leftmost bit being used as a sign bit, (a 0 being plus and 1 minus). When the sign is positive all the bits represent the absolute value of the number; and when the sign is negative, they represent the 2's complement of the absolute value of the number.
In the case of addition and subtraction the occurrence of an overflow is reflected by the carries into and out of the leftmost bit position (the sign position). If the carry into the leftmost bit position does not equal the carry out of that position then overflow has occurred. If overflow has been detected and if the sign bit equals 0, the resultant is below range; if with overflow, the sign bit equals 1, the resultant is above range.
An explicit statement about the assumed location of the binary point is necessary only for multiplication and division; for addition, subtraction, and comparison the binary points are "lined up."
In the GE-625/635 Processor, multiplication and division are implemented in two forms for 2's complement numbers: integer and fractional.
In integer arithmetic, the location of the binary point is assumed to the right of the least-significant bit position, that is, depending on the precision, to the right of bit position 35 or 71. The general representation of a fixed-point integer is then:
-an2n +an-12n-1 +an-22n-2 ... +a121 +a020
where an is the sign bit.
In fractional arithmetic, the location of the binary point is assumed to the left of the most-significant bit position, that is, to the left of bit position 1. The general representation of a fixed-point fraction is then:
-a020 +a12-1 +a22-2 ... +an-12-(n-1) +an2-n
The number ranges for the various cases of precision, interpretation, and arithmetic are listed in Figure II-3.
| Interpretation | Arithmetic | Precision | ||
|---|---|---|---|---|
| Half-Word (Xn, Y0..17) | Single-Word (A,Q,Y) | Double-Word (AQ, Y-pair) | ||
| Algebraic | Integral | -217 <= N <= (217 - 1) | -235 <= X <= (235-1) | -271 <= N <= (271-1) |
| Fractional | -1 <= N <= (1-2-17) | -1 <= N <= (1-2-35) | -1 <= N <= (1-2-71) | |
| Logic | Integral | 0 <= N <= (218)-1) | 0 <= N <= (236)-1) | 0 <= N <= (272)-1) |
| Fractional | 0 <= N <= (1-2-18)-1) | 0 <= N <= (1-2-36)-1) | 0 <= N <= (1-2-72)-1) | |
Figure II-3. Ranges of Fixed Point Numbers
Binary Floating-Point Numbers
The instruction set contains instructions for binary flaoting-point arithmetic with numbers of single-word and double-word precision. The upper 8 bits represent the integral exponent E in the 2's complement form, and the lower 28 or 64 bits represent the fractional mantissa M in 2's complement form. The notation for a floating point number Z is:
Z(2) = M(2) * 2E(2)
Single-Word precision:
0 1 7 8 9 35 ---+------------+---+-------------------------------------- | s | | s | | ---+------------+---+-------------------------------------- | E | M |
Double-Word precision:
0 1 7 8 9 71 ---+------------+---+----------------------------------------------------- | s | | s | | ---+------------+---+----------------------------------------------------- | E | M |
Where S = Sign bit
Before doing floating point additions or subtractions, the Processor aligns the number which has the smaller positive exponent. To maintain accuracy, the lowset sermissible exponint of -128 together with the mantissa equal to 0.000....0 has beed defined as the machine representation of the number zero (which has no unique floating-point representation). Whenever a floating point operation yeilds a resultant untruntcated machine mantissa equal to zero (71 bits plus sign because of extended precision), the exponent is automatically set to -128.
The general representation of the exponent for single and double precision is:
-e727+e626+ . . . +e121+e020
where e7 is the sign.
The general representations of the single- and double-precision mantissa are:
where m0 is the sign in both cases.
Normalized Floating-Point Numbers
For normalized floating point numbers, the binary point is placed at the left of the most-significant bit of the manitssa (to the right of the sign bit). Numbers are normalized by shifting the mantissa (and correspondingly adjusting the exponent) until no leading zeros are present in the mantissa for positive numbers, or until no leading ones are present in the mantissa for negative numbers. Zeros fill in the vacated bit positions. With the exception of the number zero (represented as 0 * 2-128), all normalized floating point numbers will contain a binary 1 in the most-significant bit position for positive numbers and a bianry 0 in the most-significant bit position for negative numbers. Some examples are:
| Unnormalized positive number | (0|0001101) * 27 | |
| Same number normalized | (0|1101000) * 24 | |
| Unnormalized negative number | (1|11010111) * 2-4 | |
| Same number normalized | (1|01011100) * 2-6 |
The numberof ranges resulting from the various cases of precision, normalization, and sign are listed in the table following:
| Sign | Single Precision | Double Precision | |
|---|---|---|---|
| Normalized | Positive | 2-129 <= N <= (1-2-27) 2127 | 2-129 <= N <= (1-2-63) 2127 |
| Negative | -(1+2-26)2-129= N >= -2127 | -(1+2-62)2-129= N >= -2127 | |
| Unnormalized | Positive | 2-155 <= N <= (1-2-27) 2127 | 2-191 <= N <= (1-2-63) 2127 |
| Negative | -2-155 >= N >= -2127 | -2-191 >= N >= -2127 |
NOTE: The floating-point number zero is not included in the table.
Figure II-4. Ranges of Floating-Point Numbers
Decimal Numbers
The instruction set does not comprise instructions for decimal arithmetic. The represetation of decimal numbers in the machine therefore depends entirely on the programs used for performing the decimal arithmetic required.
The representation of te decimal digits as a subset of the character set
is shown in Appendix F.
Instructions
Machine instructions have the following general format:
---------------------------+------------+---+---+---+-------------- | y | op code | 0 | i | 0 | tag | ---------------------------+------------+---+---+---+-------------- 0 17 18 26 27 28 29 30 35
Where
The three repeat instructions, Repeat, Repeat Double, and Repeat Link (RPT, RPD, and RPL) use a different instruction format. (See pages II-125, II-127, and II-129.
Indirect words have the same general format as the instruction words;
however, the fields are used in a somewhat different way. (See page II-26
and following.)
ADDRESS TRANSLATION AND MODIFICATION
Address Translation
Any program address to be used in a memory access request while the Processor is in the Slave Mode is first translated into an actual address and then submitted to the memory.
The term "program address" is used for the following addresses:
For the purpose of address translation, the Processor Base Address Register contains a base address in bit positions 0-7. The translation takes place only in the Slave Mode of operation. It consists of adding this base address to bit positions 0-7 of the program address, using the Relocation Adder (RS).
In the Master Mode no address translation takes place. Any program address to be used in a memory access request while the Processor is in the Master Mode is used directly as an actual address and submitted to the memory without any translation.
Address translation is actually based on nine bits, namely the Base
Address Register positions 0-8 and the bit positions 0-8 of the program
address; this permits address relocation by multiples of 512 words.
Because of a software requirement, bit positions 8 and 17 of the Base
Address Register have been wired in such a way that they contain
0's permanently and cannot be altered by the Load Base Address Register
(LBAR) instruction, Thus, address relocation is performed in multiples of
1024.
Tag Field
Before the operation of an instruction is carried out, an address modification procedure generally takes place as directed by the tag field of the instruction and possibly of indirect words. Only the repeat mode instructions RPT, RPD, and RPL do not provide for an address modification. (See pages II-125, II-127, and II-129.
The tag field consists of two parts, tm and td that are located within the instruction word as follows:
30 31 32 35 ---+---+---+---+---+--- | | | ---+---+---+---+---+--- | tm | td |
Where
- tm
- specifies one of the four possible modification types: Register (R), Register then Indirect (RI), Indirect then Register (IR), and Indirect then Tally (IT)
- td
- specifies further the action for each modification type:
- In the case of tm = R, RI, or IR, td is called the register designator and generally specifies the register to be used in indexing.
- In the case of tm = IT, td is called the tally designator and specifies the tallying in detail.
The following table gives a general characterization of each of the four modification types.
| tm | Binary | Modification Type |
|---|---|---|
| R | 00 | Register Indexing according to td as register designator and termination of the address modification procedure. |
| RI | 01 | Register then Indirect Indexing according to td as register designator, then substitution and continuation of the modification procedure as directed by the Tag field of this indirect word. |
| IR | 11 | Indirect then Register Saving of td as final register designator, then substitution and continuation of the modification procedure as directed by the Tag field of this indirect word. |
| IT | 10 | Indirect then Tally Substitution, then use of this indirect word according to td as tally designator. |
Each of the three modification types R, RI, IR includes an indexing step which is further specified by the register designator td In most cases, td really specifies the register from which the index is obtained. However td may also specify a different action, namely that the effective address Y is to be used directly as operand and not as address of an operand (DU, DL), or that nothing takes place at all (N). Nevertheless td is called "register designator" in these cases.
| Register Designator | Action | ||
|---|---|---|---|
| Symbolic | Binary | ||
| N | 0000 | y | replaces Y |
| X1 | 1001 | y + C(Xn) | replaces Y |
| X2 | 1010 | ||
| . | . | ||
| X7 | 1111 | ||
| AU | 0001 | y + C(A)0..17 | replaces Y |
| AL | 0101 | y + C(A)18..35 | replaces Y |
| QU | 0010 | y + C(Q)0..17 | replaces Y |
| QL | 0110 | y + C(A)18..35 | replaces Y |
| IC | 0100 | y + C(IC) | replaces Y |
| DU | 0011 | y, 00...0 | is the operand |
| DL | 0111 | 00...0,y | is the operand |
The modification type IT consists of a substitution and the use of this indirect word as specified by the td of the instruction or previous indirect word as tally designator.
The format of the indirect word is:
------------------+------------+------ | y | Tally | Tag | ------------------+------------+------ 0 17 18 29 30 35
Where
y = address field Tally = tally field Tag = tag field
Depending upon the prior tally designator, the tag field is used in one of three ways:
...
The following table gives the possible tally designators under IT type modification.
| Tally Designator | Name | |
|---|---|---|
| Symbolic | Binary | |
| I | 1001 | Indirect only |
| DI | 1100 | Decrement Address, Increment Tally |
| AD | 1011 | Add Delta (from address field) |
| SD | 0100 | Subtract Delta (from address field) |
| ID | 1110 | Increment Address, Decrement Tally |
| DIC | 1101 | Decrement Address, Increment Tally, and Continue |
| IDC | 1111 | Increment Address, Decrement Tally, and Continue |
| CI | 1000 | Character form Indirect |
| SC | 1010 | Sequence Character |
| F | 0000 | Fault |
All possible types and sequences of address modification are shown on the following two flow charts.
| Modification Type | Flow Chart |
|---|---|
| R, IR, and RI address modification | Figure 11-5A |
| IT address modification | Figure II-5B |
See explanation of symbols and descriptions of modifications immediately following these figures.
Figure II-5A. Address Modification Flowchart
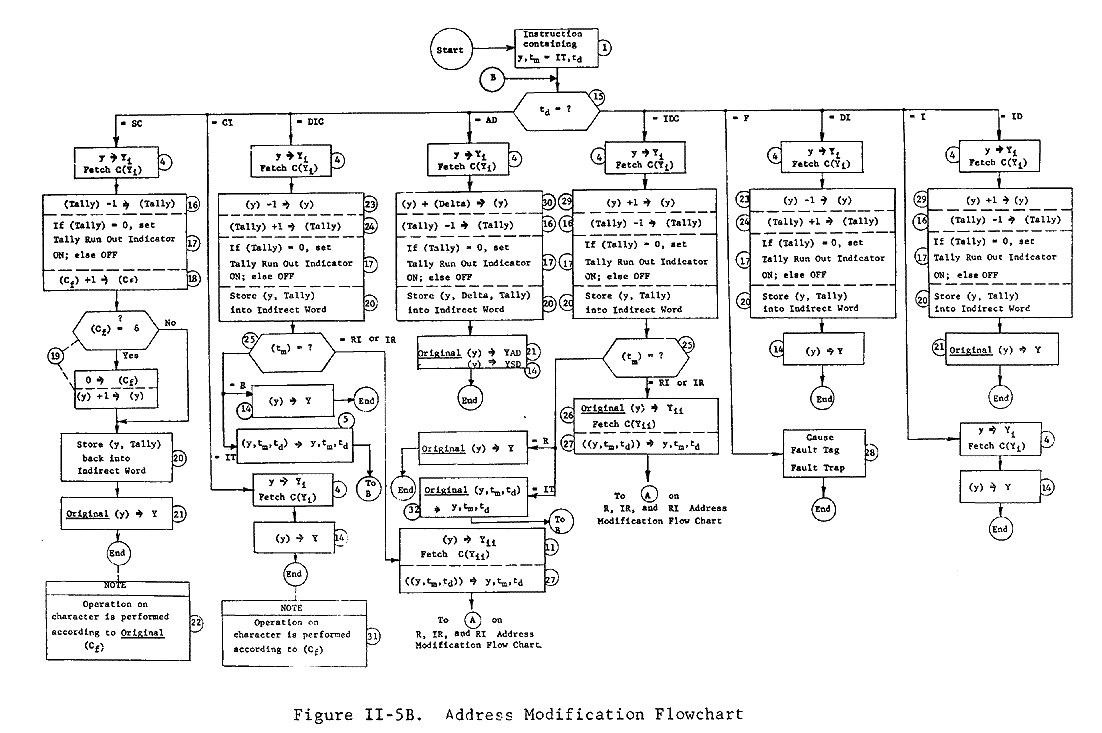
Explanation of Symbols Used on Flowcharts
| y, tm,td | is the original address, tag modifier, and tag designator, respectively. |
| Cf, Tally, Delta | is the value of the character field, tally field,and delta field of an indirect word. |
| 4 | should be read "replaces." |
| C(---) | should be read "the contents of ---." |
| Y | is the final effective address to be used in carrying out an instruction operation. |
| Yi | is the address of an indirect word which will be used for further modification. |
| Yii | is the address, obtained from another indirect word, of an indirect word which will be used for further modification. |
| (---) | represents quantities obtained from the contents of an indirect word. |
| ((---)) | represents quantities obtained from the contents of an indirect word which was obtained through another indirect word. |
| td* | is the register designator to be used as a final register modifier under IR modification. |
| Original | Most indirect words which are used under IT modification utilize the read-alter-rewrite (RAR) memory cycle. This RAR cycle must be completed before another indirect cycle can occur. The word original refers to the quantity contained in an indirect word before that quantity is incremented (during the alter part of the RAR cycle). Omission of the word original refers to the quantity after it is incremented or decremented during the alter portion of the RAR cycle. |
| End | indicates that the modification procedure for that instruction has terminated and the effective address Y, developed up to that point, is used to carry out the instruction operation. |
| 1 | The instruction word address field serves as the initial value of the tentative address y, and its tag field supplies the initial modifier tm as well as initial designator td | ||||||||||||||||||||||||||||||||||||||||||||||||||||
| 2 | tm is one of the four modification types: R, RI, IR, or IT. | ||||||||||||||||||||||||||||||||||||||||||||||||||||
| 3 | y modified by td replaces the former tentative address y. If td = DU or DL, DU or DL is ignored and the modification proceeds as if td = N. | ||||||||||||||||||||||||||||||||||||||||||||||||||||
| 4 | The tentative address y, developed up to that point, becomes the address Yi. to be used in accessing an indirect word which will be used for further modification. Using Yi the indirect word is fetched. | ||||||||||||||||||||||||||||||||||||||||||||||||||||
| 5 | The address and tag fields of the last indirect word replace the tentative address and the tag of the instruction. | ||||||||||||||||||||||||||||||||||||||||||||||||||||
| 6 |
The last designator t| 7 |
tm, of the indirect word, designates one of the four
modification types: R, RI, IR, or IT.
| 8 |
The address of the indirect word (y), modified by the final register
modifier td*, replaces the former tentative address.
| 9 |
The tentative indirect address (y), developed up to that point,
is used as the effective address Y for carrying out the instruction
operation.
| 10 |
The designator of the indirect word (td) replaces the final
register designator td*.
| 11 |
The tentative indirect address (y), developed up to that point becomes
the address Yii, to be used in accessing another indirect
word which will be used for further modification. Using Yii,
the indirect word is fetched.
| 12 |
The address (y), contained in the indirect word and modified by the
designator of the indirect word (td), replaces the
tentative indirect address (y).
| 13 |
y modified by td replaces the former tentative address y.
| 14 |
The tentative address y, developed up to that point, is used as the
effective address Y for carrying out the instruction's operation.
| 15 |
td is one of the nine tally designators: SC, CI, DIG, AD,
IDC, F, DI, I, or ID.
| 16 |
A value one less than or one greater than the value of the tally field
loaded from the indirect word becomes the new value of the tally field,
depending on the use of the AD or SD designator.
| 17 |
The Tally Runout Indicator is set to ON if the tally field equals zero
after incrementation or decrementation; the Indicator is set to
OFF if the tally field does not equal zero after incrementation
or decrementation.
| 18 |
A value one greater than the value of the character field loaded from
the indirect word becomes the new value of the character field.
| 19 |
If the value of the character field Cf equals six, the
character field is set to zero; and a value one greater than the value
of the address field loaded from the indirect word becomes the new value
of the address field.
| 20 |
During the rewrite portion of the read-alter-rewrite cycle used for
updating an indirect word, the updated fields -- (y), (Cf),
(Tally), (Delta), (tm), (td), where applicable --
are returned to storage in memory.
| 21 |
The original value of the address field (y), as loaded from the indirect
word before any incrementation or decrementation, becomes the
effective address Y which is used to carry out the instruction operation.
| 22 |
The original value of the character field Cf, as loaded from
the indirect word before any incrementation (or setting to zero),
is the value used in carrying out the instruction operation. (See note
at end of this listing.)
| 23 |
A value one less than the value of the address field loaded from the
indirect word becomes the new value of the address field.
| 24 |
A value one greater than the value of the tally field loaded from the
indirect word becomes the new value of the tally field.
| 25 |
Under IDC or DIG types of modification, the modifiers permitted within the
indirect are:
td = N
m
t = IR
td = N
m
t =RI
td = N
m
t = IT any
td
m
t = R effectively terminates the modification procedure while
m
t = RI, IR, or IT seeks at least an additional level of modification.
m
| 26 |
The original value of the address field (y), as loaded from the indirect
word before incrementation, becomes the address Yii to
be used in accessing the next indirect word which will be used for further
modification.
| 27 |
The address and tag fields of Yii replace the address and tag
fields of the original instruction, and modification proceeds as directed
by the new tag field.
| 28 |
Occurs when tm = IT and td = F, or when Fault tag
fault is initiated and no further indirect addressing occurs.
| 29 |
A value one greater than the value of the address field loaded from the
indirect word becomes the new value of the address field.
| 30 |
A value equal to the value of the address field (loaded from the indirect
word) plus or minus Delta (a constant also loaded from the indirect word)
replaces the value of the address field, The constant is positive for
the AD designator and negative for the SD designator.
| 31 |
The value of the character field Cf, after incrementation
(or setting to zero), is used in carrying out the instruction operation.
(See the note at the end of this listing.)
| 32 |
The original value of the address field and the tag field of the last
indirect word replace the tentative address and tag of the instruction.
| |
When the tally designator is CI or SC, the character field of the last indirect word is an octal number which specifies the character position of the memory location Y to be used in carrying out the instruction operation (the example uses a value of 3 in the character field).
....
For six-bit character operations in which the operand is taken from memory, the effective operand from memory is presented as a single word with the specified character justified to character position 5; positions 0-4 are presented as zero. For operations in which the resultant is placed in memory, character 5 of the resultant replaces the specified character in memory location Y; the remaining characters in memory location Y are not changed.
For nine-bit character operations in which the operand is taken from
memory, the effective operand from memory is presented as a single word
with the specified character justified to character position 3; positions
0-2 are presented as zero. For operations in which the resultant is
placed in memory, character 3 of the resultant replaces the specified
character in memory location Y; the remaining characters in memory
location Y are not changed.
CALCULATION OF INSTRUCTION EXECUTION TIMES
The instruction execution times (Appendix A) are based on fetching of instructions in pairs from memory, and in the case of overlap type instructions, also on overlap between the operation execution of the overlap type instruction and the fetching and address modification of the next instruction. (Overlap type instructions = multiplications; divisions; shifts; floating-point operations except "loads" and "stores".)
Certain operations prevent the fetching of instructions in pairs or the overlapping; accordingly, the following time adjustments should be made.
The instruction execution times of shift and floating-point operations are listed as "average times based on a number of five-shift steps. Note that a single-shift step may effect a shift by one, four, or sixteen positions. Actual times for these instructions may vary by up to + 0.8 microseconds. Where unnornialized operands are used in normalizing floating-point operations, worst-case conditions can add as much as 1.5 microseconds.
Address modifications do not require any time adjustments except in the following cases:
The GE-625/635 instruction set described under this heading is arranged by functional class, as listed in Appendix A. Appendix A together with Appendix B, which lists the instructions in alphabetical order by mnemonic, afford convenient page references to the instructions in this section, Appendix C presents the instruction mnemonics grouped by operation code.
For the description of the machine instructions that follow it is
assumed that the reader is familiar with the general structure of the
Processor, the representation of information, the data formats, and the
method of address modifications, as presented in the preceding paragraphs
of this chapter.
Format of Instruction Description
Each instruction in the repertoire is described in the following pages of this chapter. The descriptions are presented in the standardized format shown below.
| Mnemonic: | Name of the Instruction: | Op Code (octal) | |||
|
| |||||
| SUMMARY: | |||||
| MODIFICATIONS: | |||||
| INDICATORS: | (Indicators not listed are not affected) | ||||
|
| |||||
| NOTE: | |||||
This line has three headings that appear over boxes containing the following:
The following abbreviations and symbols will be used for the description of the machine operations.
Registers:
| A | - | Accumulator Register (36 bits) | |
| Q | - | Quotient Register (36 bits) | |
| AQ | - | Combined Accumulator-Quotient Register (72 bits) | |
| Xn | - | Index Register n (n = 0, 1,. . . , 7) (18 bits) | |
| E | - | Exponent Register (8 bits) | |
| EA | - | Combined Exponent-Accumulator Register (8 + 36 bits) | |
| EAQ | - | Combined Exponent-Accumulator-Quotient Register (8 + 72 bits) BAR = Base Address Register (18 bits) | |
| IC | - | Instruction Counter (18 bits) | |
| IR | - | Indicator Register (18 bits, 11 of which are used at this time) | |
| TR | - | Timer Register (24 bits) | |
| Z | - | Temporary Pseudo-result of a non-store comparative Operation. |
Effective Address and Memory Locations:
| Y | - | The effective address (18 bits) of the respective instruction. | |
| Y-pair | - | A symbol denoting that the effective address Y designates a pair of memory locations (72 bits) with successive addresses, the lower one being even. When the effective address is even, then it designates the pair (Y, Y+1), and when it is odd, then the pair (Y-1, Y). In any case the memory location with the lower (even) address contains the more significant part of a double-precision number or the first of a pair of instructions. |
Register Positions and Contents:
("R" standing for any of the registers listed above as well as for a memory location or a pair of memory locations.)
| Ri | = | the ith position of R | |
| Ri...j | = | the positions i through j of R | |
| C(R) | = | the contents of the full register R | |
| C(R)i | = | the contents of the ith position of R | |
| C(R)i...j | = | the contents of the positions i through j of R |
When the description of an instruction states a change only for a part of a register or memory location, then it is always understood that the part of the register or memory location which is not mentioned remains unchanged.
Other Symbols:
| =>i | = | replaces | |
| ::i | = | compare with | |
| ANDi | = | the Boolean connective AND (symbol A) | |
| ORi | = | OR = the Boolean connective OR (symbol V) | |
| R!= | = | the Boolean connective NON-EQUIVALENCE (or EXCLUSIVE OR) |
It is a characteristic feature of the GE-625/635 computer that an address translation takes place with each memory access when the Processor operates in the Slave Mode.
During the execution of a program, a base address is contained in the bit positions 0-7 of the Processor Base Address Register. With each memory access, this base address is added to bit positions 0-7 of the program address supplied by this program in order to generate the actual address used in accessing the memory. In this way, the address translation provides complete independence of the program address range from the actual address range that is used with a specific execution of this program.
Only when the Processor is in the Master Mode is the program address used directly as an actual address; in this case, program addresses generally refer to the Comprehensive Operating System which has allocated to it the actual address range beginning at zero.
The descriptions of the individual machine instructions in this chapter do not mention the address translation. It is understood here that an address translation has to be performed immediately prior to each memory access request (in the Slave Mode) regardless of whether:
No address translations take place for effective addresses which are
used either as operands directly or in other ways (for example, shifts).
Floating-Point Arithmetic
Numbers in floating-point representation are stored in memory as follows:
| Integer Exponent | Fractional Mantissa | |
|---|---|---|
| Single-word precision | C(Y)0...7 | C(Y)8...35 |
| Double-word precision | C(Y-pair)0...7 | C(Y-pair)8...71 |
When a floating-point number is held in the register EAQ, its mantissa length is allowed to increase to the full length of the register AQ.
....
In storing a floating-point number, a truncation of the mantissa takes
place. With single-word precision store Instructions, only
C(AQ)0-27 will be stored as mantissa, and with double-word
precision store instructions, only C(AQ)0-63.
DESCRIPTIONS OF THE MACHINE INSTRUCTIONS
| DATA MOVEMENT LOAD |
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(Y) => C(A) | |||||
| MODIFICATIONS: | All | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(Y) => C(Q) | |||||
| MODIFICATIONS: | All | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(Y-pair) => C(AQ) | |||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(Y)0...17 => C(Xn) | |||||
| MODIFICATIONS: | All except CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | |||
| |||||
| SUMMARY: |
C(Y, Yñ1, .... Y+7) => C(XO,X1,...X7,A,Q,E,TR)
where Y15-17 = 000 for the first location only and increases by one for each succeeding location. | ||||
| MODIFICATIONS: | All except DU, DL, CI, SC | ||||
| INDICATORS: | None affected | ||||
| NOTE: |
C(Y)0-17 => C(X0) C(Y)18-357 => C(X1) C(Y+1)0-17 => C(X2) C(Y+1)18-357 => C(X3) C(Y+2)0-17 => C(X4) C(Y+2)18-357 => C(X5) |
C(Y+3)0-17 => C(X6) C(Y+3)18-35 => C(X7) C(Y+4)0-35 => C(A) C(Y+5)0-35 => C(Q) C(Y+6)0-7 => C(E) C(Y+7)0-24 => C(TR) | |||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||
| ||||||||
| SUMMARY: | -C(Y) => C(A) | |||||||
| MODIFICATIONS: | All | |||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||
| ||||||||
| NOTE: | This instruction changes the number to its negative (if 0) while moving it from the memory to A. The operation is executed by forming the two's complement of the string of 36 bits. | |||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||
| ||||||||
| SUMMARY: | -C(Y) => C(Q) | |||||||
| MODIFICATIONS: | All | |||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||
| ||||||||
| NOTE: | This instruction changes the number to its negative (if 0) while moving it from Y to Q. The operation is executed by forming the two's complement of the string of 36 bits. | |||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||
| ||||||||
| SUMMARY: | -C(Y-pair) => C(AQ) | |||||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||
| ||||||||
| NOTE: | This instruction changes the number to its negative (if /= 0) while moving it from Y-pair to AQ. The operation is executed by forming the 2`s complement of the string of 72 bits. | |||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||
| ||||||||
| SUMMARY: | -C(Y)0...17 => C(Xn) | |||||||
| MODIFICATIONS: | All except CI, SC | |||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||
| ||||||||
| NOTE: | This instruction changes the number to its negative (if /= 0) while moving it from Y0...17 to Xn. The operation is executed by forming the 2`s complement of the string of 18 bits. | |||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||||||||||
| ||||||||||||||||||
| SUMMARY: | Y => C(A)0...17;
00...0 =>C(A)18...35
| MODIFICATIONS: | All except DU, DL
| INDICATORS: | (Indicators not listed are not affected)
|
|
NOTE: |
This instruction, and the instructions EAQ and
EAXn, facilitate interregister data movements;
the data source is specified by the address modification, and the
data destination by the operation of the instruction.
| | ||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||||||||||
| ||||||||||||||||||
| SUMMARY: | Y => C(Q)0...17;
00...0 =>C(Q)18...35
| MODIFICATIONS: | All except DU, DL
| INDICATORS: | (Indicators not listed are not affected)
|
|
NOTE: |
This instruction, and the instructions EAA and
EAXn, facilitate interregister data movements;
the data source is specified by the address modification,
and the data destination by the operation of the instruction.
| | ||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | Y => C(Xn) | |||||
| MODIFICATIONS: | All except DU, DL | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| NOTE: | This instruction, and the instructions EAA and EAQ, facilitate interregister data movements; the data source is specified by the address modification, and the data destination by the operation of the instruction. | |||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||||||||||||||||||||||||||
| ||||||||||||||||||||||||||||||||||
| SUMMARY: | C(Y)18..35 => C(IR) | |||||||||||||||||||||||||||||||||
| MODIFICATIONS: | All except CI, SC | |||||||||||||||||||||||||||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||||||||||||||||||||||||||
| ||||||||||||||||||||||||||||||||||
| NOTE: |
| |||||||||||||||||||||||||||||||||
 |
| DATA MOVEMENT STORE |
| Mnemonic: | Name of the Instruction: | Op Code (octal) | |||
| |||||
| SUMMARY: | C(A) => C(Y) | ||||
| MODIFICATIONS: | All except DU, DL | ||||
| INDICATORS: | None Affected | ||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | |||
| |||||
| SUMMARY: | C(Q) => C(Y) | ||||
| MODIFICATIONS: | All except DU, DL | ||||
| INDICATORS: | None Affected | ||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | |||
| |||||
| SUMMARY: | C(AQ) => C(Y-pair) | ||||
| MODIFICATIONS: | All except DU, DL, CI, SC | ||||
| INDICATORS: | None Affected | ||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | |||
| |||||
| SUMMARY: | C(Xn) => C(Y)0...17 | ||||
| MODIFICATIONS: | All except DU, DL, CI, SC | ||||
| INDICATORS: | None Affected | ||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | |||
| |||||
| SUMMARY: |
C(XO,X1,...X7,A,Q,E,TR) => C(Y, Y+1, .... Y+7)
where Y15-17 = 000 for the first location only and increases by one for each succeeding location. | ||||
| MODIFICATIONS: | All except DU, DL, CI, SC | ||||
| INDICATORS: | None Affected | ||||
| NOTE: |
| ||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | |||
| |||||
| SUMMARY: | Characters of C(A) => corresponding characters of C(Y), the character positions affected being specified in the Tag field. | ||||
| MODIFICATIONS: | No modification can take place | ||||
| INDICATORS: | None Affected | ||||
| NOTE: |
Binary ones in the Tag field of this instruction specify the character proitions of A
and Y that are affected by this instruction. The control relation is shown in the
diagram below:
.... | ||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | |||
| |||||
| SUMMARY: | Characters of C(Q) => corresponding characters of C(Y), the character positions affected being specified in the Tag field. | ||||
| MODIFICATIONS: | No modification can take place | ||||
| INDICATORS: | None Affected | ||||
| NOTE: |
Binary ones in the Tag field of this instruction specify the character proitions of Q
and Y that are affected by this instruction. The control relation is shown in the
diagram below:
.... | ||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | |||
| |||||
| SUMMARY: | Characters of C(A) => corresponding characters of C(Y), the character positions affected being specified in the Tag field. | ||||
| MODIFICATIONS: | No modification can take place | ||||
| INDICATORS: | None Affected | ||||
| NOTE: |
Binary ones in the Tag field of this instruction specify the character proitions of A
and Y that are affected by this instruction. The control relation is shown in the
diagram below:
.... | ||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | |||
| |||||
| SUMMARY: | Characters of C(Q) => corresponding characters of C(Y), the character positions affected being specified in the Tag field. | ||||
| MODIFICATIONS: | No modification can take place | ||||
| INDICATORS: | None Affected | ||||
| NOTE: |
Binary ones in the Tag field of this instruction specify the character proitions of Q
and Y that are affected by this instruction. The control relation is shown in the
diagram below:
.... | ||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||||||||||||||||||||||||||
| ||||||||||||||||||||||||||||||||||
| SUMMARY: | C(IR) => C(Y)18...35 | |||||||||||||||||||||||||||||||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||||||||||||||||||||||||||||||
| INDICATORS: | Indicators not listed are not affected | |||||||||||||||||||||||||||||||||
| NOTE: |
| |||||||||||||||||||||||||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | |||
| |||||
| SUMMARY: | C(TR) => C(Y)0...23 00...0 => C(Y)24...35 | ||||
| MODIFICATIONS: | All except DU, DL, CL, SC | ||||
| INDICATORS: | None Affected | ||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | |||
| |||||
| SUMMARY: | C(BAR) => C(Y)0...17 | ||||
| MODIFICATIONS: | All except DU, DL, CL, SC | ||||
| INDICATORS: | None Affected | ||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | |||
| |||||
| SUMMARY: | 00...0 => C(Y) | ||||
| MODIFICATIONS: | All except DU, DL, CL, SC | ||||
| INDICATORS: | None Affected | ||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||||||||||||||||||||||||||
| ||||||||||||||||||||||||||||||||||
| SUMMARY: |
| |||||||||||||||||||||||||||||||||
| MODIFICATIONS: | All except DU, DL, CL, SC | |||||||||||||||||||||||||||||||||
| INDICATORS: | Indicators not listed are not affected | |||||||||||||||||||||||||||||||||
| Note: |
| |||||||||||||||||||||||||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | |||
| |||||
| SUMMARY: |
| ||||
| MODIFICATIONS: | All except DU, DL, CL, SC | ||||
| INDICATORS: | None affected | ||||
 |
| DATA MOVEMENT SHIFT |
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | Shift right C(A) by Y11...17 positions; fill vacated with C(A)0 | |||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | Shift right C(Q) by Y11...17 positions; fill vacated with C(Q)0 | |||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | Shift right C(AQ) by Y11...17 positions; fill vacated with C(AQ)0 | |||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||
| ||||||||
| SUMMARY: | Shift left C(A) by Y11...17 positions; fill vacated with zeros. | |||||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||
| ||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||
| ||||||||
| SUMMARY: | Shift left C(Q) by Y11...17 positions; fill vacated with zeros. | |||||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||
| ||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||
| ||||||||
| SUMMARY: | Shift left C(AQ) by Y11...17 positions; fill vacated with zeros. | |||||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||
| ||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | Shift right C(A) by Y11...17 positions; fill vacated with zeros. | |||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | Shift right C(Q) by Y11...17 positions; fill vacated with zeros. | |||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | Shift right C(AQ) by Y11...17 positions; fill vacated with zeros. | |||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | Rotate C(A) by Y11...17 positions; enter each bit leaving position 0 into position 35 | |||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | Rotate C(A) by Y11...17 positions; enter each bit leaving position 0 into position 35 | |||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | Rotate C(AQ) by Y11...17 positions; enter each bit leaving position 0 into position 71 | |||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
 |
| FIXED POINT ARITHMETIC ADDITION |
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(A) + C(Y) => C(A) | |||||||||
| MODIFICATIONS: | All | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(Q) + C(Y) => C(Q) | |||||||||
| MODIFICATIONS: | All | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(AQ) + C(Y-pair) => C(AQ) | |||||||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(Xn) + C(Y)0...17 => C(Xn) | |||||||||
| MODIFICATIONS: | All except CI, SC | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(A) + C(Y) => C(Y) | |||||||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(Q) + C(Y) => C(Y) | |||||||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(Xn) + C(Y)0...17 => C(Y)0...17 | |||||||||
| MODIFICATIONS: | All except DU, DL, JCI, SC | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(A) + C(Y) => C(A) | |||||||||
| MODIFICATIONS: | All | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| NOTE: | This instruction is identical to the ADA instruction with the exception that the Overflow Indicator is not affected by this instruction. | |||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(Q) + C(Y) => C(Q) | |||||||||
| MODIFICATIONS: | All | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| NOTE: | This instruction is identical to the ADQ instruction with the exception that the Overflow Indicator is not affectedby this instruction. | |||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(AQ) + C(Y-pair) => C(AQ) | |||||||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| NOTE: | This instruction is identical to the ADAQ instruction with the exception that the Overflow Indicator is not affected by this instruction. | |||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||||||||||||||
| ||||||||||||||||||||||
| SUMMARY: | C(Xn) + C(Y)| MODIFICATIONS: | All except CI, SC
| INDICATORS: | (Indicators not listed are not affected)
|
|
NOTE: | This instruction is identical to the
ADXn instruction with the exception that the Overflow
Indicator is not affected by this instruction.
| | ||||||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: |
| |||||||||
| MODIFICATIONS: | All | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| NOTE: | This instruction is identical to the ADA instruction with the exception that when the Carry Indicator is ON at the beginning of the instruction, then a 1 is added to the least significant position. | |||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: |
| |||||||||
| MODIFICATIONS: | All | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| NOTE: | This instruction is identical to the ADQ instruction with the exception that when the Carry Indicator is ON at the beginning of the instruction, then a 1 is added to the least significant position. | |||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: |
C(AQ) + C(Y), right adjusted, => C(AQ) (See description below) | |||||||||
| MODIFICATIONS: | All except CI, SC | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| DESCRIPTION: |
A 72 bit number is formed:
C(Y0,C(Y0, ....., C(Y0., C(Y) Its lower half (bits 35 - 71) is identical to C(Y), and each of the bits of its upper half (bits 0 - 35) is identical to the sign bit of C(Y), i.e. to C(Y0). This number is added to the contents of the combined AQ-register, efecting the addition of C(Y) to the lower half of the combined AQ-register, with a possible cvarry out of the Q -part being passed on to the A-part. | |||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(Y) + 0 .... 01 => C(Y) | |||||||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
 |
| FIXED POINT ARITHMETIC
SUBTRACTION |
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(A) - C(Y) => C(A) | |||||||||
| MODIFICATIONS: | All | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(Q) - C(Y) => C(Q) | |||||||||
| MODIFICATIONS: | All | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(AQ) - C(Y-pair) => C(AQ) | |||||||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(Xn) - C(Y)0...17 => C(Xn) | |||||||||
| MODIFICATIONS: | All except CI, SC | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(A) - C(Y) => C(Y) | |||||||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(Q) - C(Y) => C(Y) | |||||||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(Xn) - C(Y)0...17 => C(Y)0...17 | |||||||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(A) - C(Y) => C(A) | |||||||||
| MODIFICATIONS: | All | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| NOTE: | This instruction is identical to the SBA instruction with the exception that the Overflow Indicator is not affected by this instruction. | |||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(Q) - C(Y) => C(Q) | |||||||||
| MODIFICATIONS: | All | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| NOTE: | This instruction is identical to the SBQ instruction with the exception that the Overflow Indicator is not affectedby this instruction. | |||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: | C(AQ) - C(Y-pair) => C(AQ) | |||||||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| NOTE: | This instruction is identical to the SBAQ instruction with the exception that the Overflow Indicator is not affected by this instruction. | |||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||||||||||||||
| ||||||||||||||||||||||
| SUMMARY: | C(Xn) - C(Y)| MODIFICATIONS: | All except CI, SC
| INDICATORS: | (Indicators not listed are not affected)
|
|
NOTE: | This instruction is identical to the
SBXn instruction with the exception that the Overflow
Indicator is not affected by this instruction.
| | ||||||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: |
| |||||||||
| MODIFICATIONS: | All | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| NOTE: |
| |||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||||
| ||||||||||
| SUMMARY: |
| |||||||||
| MODIFICATIONS: | All | |||||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||||
| ||||||||||
| NOTE: |
| |||||||||
 |
| FIXED POINT ARITHMETIC
MULTIPLICATION |
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(Q) * C(Y) => C(AQ) right-adjusted | |||||
| MODIFICATIONS: | All except CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| NOTES: |
| |||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||
| ||||||||
| SUMMARY: | C(A) * C(Y) => C(AQ) left-adjusted | |||||||
| MODIFICATIONS: | All except CI, SC | |||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||
| ||||||||
| NOTES: |
| |||||||
 |
| FIXED POINT ARITHMETIC
DIVISION |
| Mnemonic: | Name of the Instruction: | Op Code (octal) | |||||||||
| |||||||||||
| SUMMARY: |
| ||||||||||
| MODIFICATIONS: | All | ||||||||||
| INDICATORS: | (Indicators not listed are not affected) | ||||||||||
| |||||||||||
| NOTES: |
| ||||||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | |||||||||
| |||||||||||
| SUMMARY: |
| ||||||||||
| MODIFICATIONS: | All | ||||||||||
| INDICATORS: | (Indicators not listed are not affected) | ||||||||||
| |||||||||||
| NOTES: |
| ||||||||||
 |
| FIXED POINT ARITHMETIC
NEGATE |
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||
| ||||||||
| SUMMARY: | -C(A) => C(A) | |||||||
| MODIFICATIONS: | Are without any effect on th eoperation | |||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||
| ||||||||
| NOTE: | This instruction changes the number in A to its negative (if /= 0). The operation is executed by forming the two's complement of the string of 36 bits. | |||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||||
| ||||||||
| SUMMARY: | -C(AQ) => C(AQ) | |||||||
| MODIFICATIONS: | Are without any effect on th eoperation | |||||||
| INDICATORS: | (Indicators not listed are not affected) | |||||||
| ||||||||
| NOTE: | This instruction changes the number in AQ to its negative (if /= 0). The operation is executed by forming the two's complement of the string of 72 bits. | |||||||
 |
| BOOLEAN OPERATIONS
AND |
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(A)i AND C(Y)i => C(A)i for all i = 0, 1, ..., 35 | |||||
| MODIFICATIONS: | All | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(Q)i AND C(Y)i => C(Q)i for all i = 0, 1, ..., 35 | |||||
| MODIFICATIONS: | All | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(AQ)i AND C(Y-pair)i => C(AQ)i for all i = 0, 1, ..., 71 | |||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(Xn)i AND C(Y)i => C(Xn)i for all i = 0, 1, ..., 17 | |||||
| MODIFICATIONS: | All except CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(A)i AND C(Y)i => C(Y)i for all i = 0, 1, ..., 35 | |||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(Q)i AND C(Y)i => C(Y)i for all i = 0, 1, ..., 35 | |||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(Xn)i AND C(Y)i => C(Y)i for all i = 0, 1, ..., 17 | |||||
| MODIFICATIONS: | All except DU, DL, JCI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
 |
| BOOLEAN OPERATIONS
OR |
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(A)i OR C(Y)i => C(A)i for all i = 0, 1, ..., 35 | |||||
| MODIFICATIONS: | All | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(Q)i OR C(Y)i => C(Q)i for all i = 0, 1, ..., 35 | |||||
| MODIFICATIONS: | All | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(AQ)i OR C(Y-pair)i => C(AQ)i for all i = 0, 1, ..., 71 | |||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(Xn)i OR C(Y)i => C(Xn)i for all i = 0, 1, ..., 17 | |||||
| MODIFICATIONS: | All except CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(A)i OR C(Y)i => C(Y)i for all i = 0, 1, ..., 35 | |||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(Q)i OR C(Y)i => C(Y)i for all i = 0, 1, ..., 35 | |||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(Xn)i OR C(Y)i => C(Y)i for all i = 0, 1, ..., 17 | |||||
| MODIFICATIONS: | All except DU, DL, JCI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
 |
| BOOLEAN OPERATIONS
EXLUSIVE OR |
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(A)i /= C(Y)i => C(A)i for all i = 0, 1, ..., 35 | |||||
| MODIFICATIONS: | All | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(Q)i /= C(Y)i => C(Q)i for all i = 0, 1, ..., 35 | |||||
| MODIFICATIONS: | All | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(AQ)i /= C(Y-pair)i => C(AQ)i for all i = 0, 1, ..., 71 | |||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(Xn)i OR C(Y)i => C(Xn)i for all i = 0, 1, ..., 17 | |||||
| MODIFICATIONS: | All except CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(A)i /= C(Y)i => C(Y)i for all i = 0, 1, ..., 35 | |||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(Q)i /= C(Y)i => C(Y)i for all i = 0, 1, ..., 35 | |||||
| MODIFICATIONS: | All except DU, DL, CI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
| Mnemonic: | Name of the Instruction: | Op Code (octal) | ||||
| ||||||
| SUMMARY: | C(Xn)i /= C(Y)i => C(Y)i for all i = 0, 1, ..., 17 | |||||
| MODIFICATIONS: | All except DU, DL, JCI, SC | |||||
| INDICATORS: | (Indicators not listed are not affected) | |||||
| ||||||
 |
| COMPARISON
COMPARE |
The GE-625/635 macro assembly program is a program which will translate symbolic machine language convenient for programmer use into absolute or relocatable binary machine instructions. The symbolic language is sufficiently like machine language to permit the programmer to utilize all the facilities of the computer which would be available to him if he were to code directly in machine language.
An Assembler resembles a compiler in that it produces machine language programs. It differs from a compiler in that the symbolic language used with an Assembler is closely related to the language used by the computer, while the source language used with a compiler resembles the technical language in which problems are stated by human beings.
Compilers have several advantages over Assemblers. The language used with the compiler is easier to learn and is oriented toward the problem to be solved. The user of a compiler usually does not need an intimate knowledge of the inner workings of the computer. Programming is faster. Finally, the time required to obtain a finished, working program is greatly reduced since there is less chance for the programmer to make mistakes. The Assembler compensates for its disadvantages by offering those programmers, who need a great degree of flexibility in writing their programs, that flexibility which is not currently found in compilers.
The GE-625/635 Macro Assembler is being provided to give the professional programmers some of the conveniences of a compiler and the flexibility of an Assembler. The ability to design desired MACROs in order to provide convenient shorthand notations plus the use of all GE-625/635 machine instructions as well as a complete set of pseudo-operations provides the programmer with a very powerful and flexible tool. The output options enable him to obtain binary text in relocatable as well as absolute formats.
This Assembler is implemented in the classic format of Macro Assemblers with several variations. There are two passes over the external text: the first pass allows for updating and or merging of an ALTER package to a previously prepared assembly input. The ALTER package consists of changes to be made to the previous assembly under control of ALTER cards. During pass one, all symbols are collected and assigned their absolute or relocatable values relative to the current location counter. MACRO prototypes are processed and placed in the MACRO skeleton table immediately ready for expansion. All MACRO calls, therefore, are expanded in pass one, allowing the MACRO skeleton table to be destroyed prior to pass two.
Machine operation codes, pseudo-operations, and MACRO names are all carried in the operation table during pass one.
This implies that all operation codes, machine or pseudo, along with MACROs are looked up during pass one, and that the general operation table is destroyed at the end of pass one. The literal pool is completely expanded during pass one, avoiding duplicates (except for V3 M, and nH literals where n is greater than 12), which are assigned unique locations in pass one and will be later expanded in pass two. Double-precision numbers in the literal pool start at even locations.
At the end of pass one, the symbol table is sorted; and a complete readjustment of symbols by their relative location counter is performed. The preface card is then punched.
All instructions are generated during pass two. This is accomplished by performing a scan over the variable fields and address modifications. This information is then combined with the operation code from pass one by using a Boolean OR function. Apparent errors are flagged.
The symbolic cross-reference table is created as the variable fields are scanned and expanded. The final edit of the symbol table is done at the end of pass two. Generative pseudo-operations are processed with the conversion being done in pass two. Pseudo-operations are available to control punching of binary cards and printing images of source cards. Images of source cards in error will be printed, regardless of control pseudo-operations. Undefined symbols, and error conditions will be noted at the end of the printer listing.
The classic format of a variable field symbolic assembly program is used throughout the GE-625/635 Macro Assembler. Typically, a symbolic instruction consists of four major divisions; location field, operation field, variable field, and comments field.
The location field normally contains a name by which other instructions
may refer to the instruction named. The operation field contains the name
of the machine operation, pseudo-operation or Macro. The variable field
normally contains the location of the operand. The comments field exists
solely for the convenience of the programmer and plays no part in the
assembly process. An identification field is provided to give a means of
identifying the location of a card within a deck.
RELOCATABLE AND ABSOLUTE ASSEMBLIES
The Macro Assembler program processes inputs of several types: (1) FORTRAN IV compilations that have been translated into the Assembler language, (2) COBOL-61 compilations translated into the Assembler language, (3) source programs written originally in the Assembler language, (4) compressed source decks (COMDEK) for any of items (1) through (3) and (5) correction (ALTER) cards for any of (1) through (3). The normal operating mode of the Assembler in processing input subprograms of the types indicated above is relocatable; that is, each subprogram in a job stream is handled individually and is assigned memory locations nominally beginning with zero and extending to the upper limit required for that subprogram. Since a job stream can contain many such subprograms, it is apparent that they cannot all be loaded into a memory area starting with location zero; they must be loaded into different memory areas. Furthermore, they must be movable (relocatable) among the areas. Then for relocatable subprograms, the Assembler must provide (1) delimiters idenitifying each subprogram, (2) information specifying that the subprogram is relocatable, (3) the length of the subprogram, and (4) relocation control bits for both the upper and lower 18 bits of each assembled word.
Subprogram delimiters are the Assembler output cards $ OBJECT, heading the subprogram assembly, and $ DKEND, ending the assembly. An assembly is designated as relocatable on a card-to-card basis by a unique 3-bit Assembler punched code value in each binary output card. (See descriptions of Binary Punched Cards, page III- 84 and following.) The subprogram length is punched in the preface card(s) which immediately follows the $ OBJECT card of each subprogram. The relocation control bits are grouped together on the binary card and are referenced by GELOAD while it is loading the subprogram into absolute memory locations.
The Assembler designates that the assembly output is absolute on a card-to-card basis by punching a unique 3-bit code value in each card. This value causes GELOAD to regard all addresses on a card as actual (physical) memory addresses relative to the Base Address Register and to load accordingly. Each absolute subprogram assembly begins with a $OBJECT card and terminates with the $ DKEND card, as in the case of relocatable assemblies.
The normal Assembler operating mode is relocatable; it is set to the
absolute mode by progranimer use of ABS.
ASSEMBLY LANGUAGE PROGRAMMING
Location Field
In machine instruction or MACROS this location may contain a symbol or
may be left blank, if no reference is made to the instruction. (With
certain pseudo-operations, this field has a special use and is described
later in this publication.) Associated with the location field is a
one-character field which allows the programmer to specify whether this
generated machine word should fall in a special memory location. If this
is left blank, then the instruction will be located in the next available
location. But, if there is an 0 in this field, the instruction will be
located at the next available odd location; if an E, then at the next
available even location; if the number 8, then in the next location which
is a multiple of eight.
Operation Field
The operation field may contain from zero to six characters taken from the set 0-9, A-Z, and the period (.). The group of characters must be: (1) a legal GE-625/635 operation, * (2)a Macro Assembler pseudo-operation or (3) programmer macro operation code. The character group must begin in column eight (left-justified) and must be followed by at least one blank.
A blank field or the special code ARG will be interpreted as a zero operation, and the operation field will be all zeros in the assembly coding. Anything appearing in the operation field which is not in (1), (2), or (3) above is an “illegal” operation and will result in an error flag in the assembly listing.
*All indexing instructions (LDX, STX, ADX, etc.) may be used without the index register number appended. In this case there are three subfields in the variable field. The first subfield is an expression which when evaluated will designate the proper index register. Thus,
LDX 1,5,DUis equivalent to
LDX1 5, DUalso, the following is admissible:
LDX B+A, 5, DU
The variable field contains one or more subfields that are separated by the programmer through the use of commas placed between subfields. The number and type of subfields vary depending upon the content of the operation field: (1) machine instruction, (2) Macro Assembler pseudo-operation, or (3) macro operation.
The subfields within the variable field of GE-625/635 machine instructions consist of the address and the tag (modifier). The address may be any legitimate expression or a literal. This is the first subfield of the variable field and is separated from the tag by a comma. Through address modification, as directed by the tag, a program address is defined. This program address is either (1) an instruction address used for fetching instructions, (2) a tentative address used for fetching an indirect word, or (3) an effective address used for obtaining an operand or storing a result.
The subfields used with pseudo-operations vary considerably; they are described individually in this publication under each pseudo-operation. Subfields used with macro operations are substitutable arguments which, in themselves, may be instructions, operand addresses, modifier tags, pseudo-operations, or other macro operations. All of these types of subfields are presented in the discussion on macro operations.
The first character of the variable field must begin by column 16.
The end of the variable field is designated by the first blank character
encountered in the variable field (except for the BCI instruction and in
the use of Hollerith literals). If any subfield is null (no entry given
when one is needed), it is interpreted to be zero.
The comments field exists solely for the convenience of the programmer;
it plays no part in the assembly process. Programmer comments follow the
variable field and are separated from that field by at least one blank
column.
This field is used or not used according to programmer option.
Its intended use is for instruction identification and sequencing.
Symbolic instructions are punched one per card, each card representing
one line of the coding sheet (Figure III-1). The following is a breakdown
of the card columns normally used.
Comments Field
Identification Field
SYMBOLIC CARD FORMAT
| Columns | 1 - 6 | Location field | |
| Column | 7 | Even/odd subfield | |
| Columns | 8 - 13 | Operation field | |
| Columns | 14 - 15 | Blank | |
| Columns | 16 - Blank* | Variable field | |
| Column | Blank - 72 | Comments field (separated from variable field by at least one blank) | |
| Columns | 73 - 80 | Identification field |
* First blank column encountered within an expression will terminate the processing of the variable field.
[ *missing image* ]
Figure III-1. GE-625/635 Macro Assembler Coding Form
A symbol is a string of from one to six nonbiank characters, at least one of which is nonnumeric, and the first of which is non-zero. The characters must be taken from the set made up of 0-9. A-Z and the period (.). Symbols can appear in the location and variable fields of the Assembler coding form. (Symbols are also known as location symbols and symbolic addresses.)
Symbols are defined by:
Every symbol used in a program must be defined exactly once, except for those symbols which are initially defined and redefined by the SET pseudo-operation. An error will be indicated by the Assembler if any symbol isreferencedbut never defined, or if any symbol is defined more than once.
The following are examples of permissible symbols:
A A1000 E1XP3 A..... Z FIRST .XP3 B.707 B1 ALOGlO ADDTO 1234X ERR BEGIN ERROR 3.141P
Symbols are classified into four types:
The smallest component of a complete expression is an element.
An element consists of a single symbol or an integer less than
235. (The asterisk may also be used as an element; see below.)
Terms
A term is a string composed of elements and operators. It may consist of one element or, generally speaking, n elements separated by n - 1 operators of the type * and where * indicates multiplication and / indicates division. If a term does not begin with an element or end with an element, then a null element will be assumed. It is not permissible to write two operators in succession or to write two elements in succession.
Examples of terms are:
M MAN*T 7*y
436 BETA/3 A*B*C/X*Y*Z
START 4*AB/ROOT ONE*TWO/THREE
An asterisk (*) may be used as an element in addition to being used as an operator. When it is used as an element, it refers to the location of the instruction in which it appears. For example, the instruction
A1O TRA *+2
is equivalent to
A1O TRA A10+2
and represents a transfer to the second location following the transfer
instruction. There is no ambiguity between this usage of the asterisk as
an element and its use as the operator for multiplication since the
position of the asterisk always makes clear what is meant. Thus, **M
means "the location of this instruction multiplied by the element M",
and the ** means "the location of this instruction times the null element"
and would be equal to zero. The notation *-* means "the location of this
instruction minus the location of this instruction." (See description of
+ and - operators below.)
An algebraic expression is a string composed of terms separated by the operators + (addition) and - (subtraction). Therefore, an expression may consist of one term or, more generally speaking, n terms separated by n - 1 operators of the type + and -. It is permissible to write two operators, plus and minus, in succession and the Assembler will assume a null element between the two operators. If no initial term or final term is stated, it will be assumed to be zero. An expression may begin with the operator plus or minus but if not explicitly given + will be assumed. Examples of permissible algebraic expressions are:
A B+4 CX*DY+EX/FY-100
SINE 7 -EXP*FUNC/LOGX+XYZ/10-SINE
XYZ +99 -X/Y *+5*X (Note: the first asterisk refers to
the instruction location)
A-3 -88 X*Y -- (Note: equivalent to zero minus zero
minus zero)
An algebraic expression is evaluated as follows: first, each symbolic
element is replaced by its numerically-defined value; then, each term is
computed from left-to-right in the order of its occurrence. In division,
the integral part of the quotient is retained; the remainder is immediately
discarded. For example, the value of the term 7 / 3 * 3 is 6. Tn the
evaluation of an expression division by zero is equivalent to division by
one and is not regarded as an error. After the evaluation of terms, they
are combined in a left-to-right order with the initial term of the
expression assumed to be zero followed by the plus operator. If there is
no final term, a null term will be used. At the completion of the expression
evaluation, the Assembler reduces the result by modulo 2n
where n is the number of binary bits in the field being defined, 18 for
address field evaluations and variable according to specified field size
for the VFD pseudo-operation. Grouping by parentheses is not permitted, but this
restriction may often be circumvented.
Boolean Expressions
A Boolean expression is defined similarly to an algebraic expression except that the operators *, /, +, or - are interpreted as Boolean operators. The meaning of these operators is defined below:
A Boolean expression is evaluated following the same procedure used for an algebraic expression except that the operators are interpreted as Boolean.
In a Boolean expression, the form operators +, -, *, and / have Boolean meanings, rather their their normal arithmetic meanings, as follows:
| Operator | Meaning | Definition |
|---|---|---|
| + | OR, INCLUSIVE OR, union | 0 + 0 = 0
0 + 1 = 1 1 + 0 = 1 1 + 1 = 1 |
| - | EXCLUSIVE OR symmetric difference | 0 - 0 = 0
0 - 1 = 1 1 - 0 = 1 1 - 1 = 0 |
| * | AND, intersection | 0 * 0 = 0
0 * 1 = 0 1 * 0 = 0 1 * 1 = 1 |
| / | 1's complement, complement, NOT | /0 = 1
/1 = 0 |
Although / is a unary operation involving only one term, by convention A/B is taken to mean A*/B; and the A is ignored. This is not regarded as an error by the Assemblers Thus, the table for / as a two-term operation is:
0/0 = 0 1/0 = 1
0/1 = 0 1/1 = 0
other conventions are:
+A = A+ = A
-A = A- = A (possible error--operand missing)
*A = A* = 0
A/ = A/0 = A
Expression evaluation can result in either relocatable or absolute values. There are three types of relocatable expressions; program relocatable (R), BLANK COMMON relocatable (C), and LABELED COMMON relocatable (L). The rules by which the Assembler determines the relocation validity of an expression are of necessity a little complex, and the presence of multiple location counters compounds the problem somewhat. Certain of the principle pseudo-operations impose restriction as to type of expression that is permissible; these are described separately under each of the affected pseudo-operations. These are:
EQU MAX BFS DUP
SET BOOL ORG FEQU
MIN BSS BEGIN
The following ten rules summarize the conditions and restrictions
governing the admissibility of relocation:
These ten rules are not a complete set of determinants but do serve as a basis for establishing a method of defining relocation admissibility of an expression.
Let Rr denote a program-text relocatable element, Rc denote a BLANK COMMON element, and Rl denote a LABELED COMMON element. Next, take any expression and process it as follows:
In the illustrative examples following, assume ALPHA and BETA to be normal relocatable elements (Rr), GAMMA and DELTA to be BLANK COMMON relocatable elements (Rc), and EPSILON and ZETA to be LABELED COMMON relocatable elements (Rl). Let N and K be absolutely equivalent to 5 and 8, respectively.
4*ALPHA-7-4*BETAreduces to
N*ALPHA+8*GAMMA+21-K*DELTAreduces to
EPSILON+N-ZETA
ALPHA-GAMMA+DELTA+7reduces to
Since all symbols defined as other than trivially equal to some number (A EQU 4), are defined relative to some explicit or implied location counter (USE, BLOCK), and are subject to adjustment at the end of pass 1, they are considered to be relocatable in pass 1, even in an absolute assembly.
Thus, special action must be taken, occasionally, if they are to be referenced and used in pass 1 by certain pseudo-operations. In particular, those pseudo-operations which call for an expression evaluation for the determination of some count subfield, the result of which must be absolute. As an example, consider
ECI 3, HOLLERITH TEXT
DUP 5, 2
Normally, the count fields in the above are nonvariant and there is no
problem. Consider however
M ECI N, HOLLERITH TEXT
DUP N, M-1
The Assembler is equipped to handle expressions in these count fields,
provided the result is absolute. But, since in the above example
M is a location symbol, and its value relative to the origin of the
USE is all that is known in pass 1, a relocation error would result.
The solution to this problem is simply to define some symbol at the
first available location of the counter in question.
It has a value of zero relative to the origin of that counter and may
be used as follows:
USE CTR
FIRST NULL
M BCI N, HOLLERITH TEXT
DUP N, M-FIRST-1
The result of this expression is now absolute, and truly represents the
pass 1 value of the symbol M (less 1).
A literal in a subfield is defined as being the data to be operated on rather than an expression which points to a location containing the data.
A programmer frequently must refer to a memory location containing a program constant. For example, if the constant 2 is to be added to the accumulator, the number 2 must be somewhere in memory. Data generating pseudo-operations in the Macro Assembler enable the programmer to introduce data words and constants into his program; but often the introduction is more directly accomplished by the use of the literal that serves as the operand of a machine instruction. Thus, the literal is data itself.
The Assembler retains source program literals by means of a table called a literal pool. When a literal appears, the Assembler prepares a constant which is equivalent in value to the data in the literal subfield. This constant is then placed in the literal pool, providing an identical constant has not already been so entered. If the constant is placed in the literal pool, it is assigned an address; and this address then replaces the data in the literal subfield, the constant being retained in the pool. If the constant is already in the literal pool, the address of the identical constant replaces the data in the literal subfield.
The Assembler processes five types of literals: decimal, octal,
alphanumeric, instruction, and variable field. The appearance of an
equal sign (=) in column 16 of the variable field instructs the
Assembler that the subfield immediately following is a literal.
The instruction and variable-field literal are placed in the
literal pool; because they cannot be evaluated until pass two of
the assembly, no attempt is made to check for duplicate entries
into the pool. Literals on the CALL and TALLY pseudo-operations
are restricted to decimal, octal, and alphanumeric where the character
count is less than 13.
Decimal Literals
Principle part -- is a signed or unsigned decimal number written with a decimal point. The decimal point is mandatory unless the exponent field is present. The decimal point may appear anywhere within the principle part. If absent, it is assumed to be at the right-hand end.
Exponent part -- if present, follows the principle part and consists of the letter E, followed by a signed or unsigned decimal integer. The floating-point number is distinguished by the presence of an E, or a decimal point, or both.
The format of the double-precision floating-point number is identical to the normal single-precision format with two exceptions:
The Assembler will ensure that all double-precision numbers begin in even memory locations. Ambiguity of storage assignment as to even or odd will always cause the Assembler to force double-precision word pairs to even locations; it will then issue a warning in the printout listing.
Examples of decimal literals are:
=-1O Integer
=26.44167E-1 Single-precision floating-point
=1.27743675385D0 Double-precision floating-point
=22.5B5 Fixed-point
The octal literal consists of the character 0 followed by a signed or unsigned octal integer. The octal integer may be from one to twelve digits in length plus the sign. The Assembler will store it in a word, right-justified. The word will be stored in its real form and will not be complemented if there is the presence of a minus sign. The sign applies to bit 0 only.
Examples of octal literals are:
=01257
=0-377777777742
The alphanumeric, or Hollerith, literal consists of the letters H or kH, where k is a character count followed by the data. If there is no count specified, a literal of exactly six 6-bit characters including blanks is assumed to follow the letter H. If a count exists, the k characters following the character H are to be used as the literal. If the value k is not a multiple of six, the last partial word will be left-justified and filled in with blanks. The value k can range from 1 through 53. (Imbedded blanks do not terminate scanning of the cards by the Assembler.)
Examples of alphanumeric literals are:
=HALPHA1
=HGONE
=4HGONE~~ (~represents a blank)
=7HTHE~END
The instruction literal consists of the character = followed by the letter, M. This is followed in turn by an operation code, one blank, and a variable field. (The imbedded blank does not terminate scanning of the card in this instance.)
Examples of instruction literals are:
=MARG~BETA
=MLDA~5,1
Instructions containing instruction literals cannot make use of any of
the forms of tag modifier, since if a modifier is encountered it is
assumed to be a part of the instruction literal.
The variable field literal begins with the letter V. Reference should be made to the description of the VFD pseudo-operation for the detailed description of using variable field data description. The subfields of a variable field literal may be one of three types: Algebraic, Boolean, and Alphanumeric.
Examples of variable field literals are:
=V10/895,5/37,H6/C,15/ALPHA
=V18/ALPHA,O12/235,6/0
Instructions containing variable field literals cannot make use of any of
the forms of a tag modifier.
When a literal is used with the modifier variations DU or DL, the value of the literal is not stored in the literal pool but is truncated to an 18-bit value, and is stored in the address field of the machine instruction. Normally, a literal represbnts a 36-bit number. For the DU or DL modifier variations, if the literal is a floating-point number or Hollerith, then bit 0-17 of the literal will be stored in the address field. In the case of all other literals, bits 18-35 of the literal will be stored in the address field.
Examples of literals modified by DU and DL are:
| CODED LITERAL | RESULTANT ADDRESS FIELD (OCTAL) |
|---|---|
=100,DL | 000144 |
=-10,DU | 001000 |
=320.,DU | 022500 |
=0.,DU | 400000 |
=077,DU | 000077 |
=2B25,DU | 004000 |
=3HOOA,DL | 000021 |
Processor instructions written for the Assembler consist of a symbol (or blanks) in the location field, a 3-to 6-character alphanumeric code representing a GE-625/635 operation in the operation field, and an operand address, (symbolic or numeric), plus a possible modifier tag in the variable field. (Legal symbols used in the location field and as operand addresses in the variable field are described on page 111-5 and following.)
Standard machine mnemonics are entered left-justified in the operation field. These are any instruction mnemonic, as presented in the listings comprising Appendices A and C.
Several Assembler pseudo-operations are closely related to machine instructions. These are:
The operand address and modifier tag of most machine instructions
comprise the subfield entries of the variable field. The address portion
may be any legitimate expression, described earlier. The address is the
first subfield in the variable field and begins in column 16. The modifier
tag subfield is separated from the address subfield by a comma. Coding of
the modifier tag subfield entries is described on the pages following.
Address Modification Features
| MODIFICATION TYPE | CODING SHEET MNEMONIC | BINARY FORMS |
|---|---|---|
--+-+-+-+-----------------
| | | | Tag |
|z|i|z+-----+-----------
| | | | tm | td |
--+-+-+-+-----+-----------
30 31 32 35
| ||
| R | BETA,(R) |
--+-+-+-+-----------------
| | | | Tag |
|z|i|z+-----+-----------
| | | | 0 0 | td |
--+-+-+-+-----+-----------
30 31 32 35
|
| RI | BETA,(R)* |
--+-+-+-+-----------------
| | | | Tag |
|z|i|z+-----+-----------
| | | | 0 1 | td |
--+-+-+-+-----+-----------
30 31 32 35
|
| IR | BETA,*(R) |
--+-+-+-+-----------------
| | | | Tag |
|z|i|z+-----+-----------
| | | | 1 1 | td |
--+-+-+-+-----+-----------
30 31 32 35
|
| IT | BETA,(T) |
--+-+-+-+-----------------
| | | | Tag |
|z|i|z+-----+-----------
| | | | 1 0 | td |
--+-+-+-+-----+-----------
30 31 32 35
|
The parentheses in (R) and (T) indicate that substitutions are made by
the programmer for R and T; these are explained under the separate
discussions of R, IR, RI, and IT modification. Binary equivalents of the
substitution are used in the td subfield.
Register (R) Modification
Simple R-type address modification is performed by the Processor whenever the programmer codes an R-type variation (listed below) and causes the Assembler to place binary zeros in both positions of the modifier subfield tm of the general instruction. Accordingly, one among 16 variations under R will be performed by the Processor, depending upon bit configurations generated by the Assembler and placed in the designator subfield (td) of the general instruction. The 16 variations, their mnemonic substitutions used on the Assembler coding sheet, the td field binary forms presented to the Processor, and the effective addresses Y generated by the Processor are indicated in the following table.
A special kind of address modification variation is provided under R modification. The use of the instruction address field as the operand is referred to as direct operand address modification, of which there are two types; (1) Direct Upper and (2) Direct Lower, With the Direct Upper variation, the address field of the instruction serves as bit positions 0-17 of the operand and zeros serve as bit positions 18-35 of the operand. With the Direct Lower variation, the address field of the instruction serves as bit positions 18-35 of the operand and zeros serve as bit positions 0-17 of the operand.
| MODIFICATION VARIATION | MNEMONIC SUBSTITUTION | BINARY FORM (td FIELD) | EFFECTIVE ADDRESS | |
|---|---|---|---|---|
| (R) | =X0 | 0 | 1000 | Y=y+C(X0)0...17 |
| =X1 | 1 | 1001 | Y=y+C(X1)0...17 | |
| =X2 | 2 | 1010 | Y=y+C(X2)0...17 | |
| =X3 | 3 | 1011 | Y=y+C(X3)0...17 | |
| =X4 | 4 | 1100 | Y=y+C(X4)0...17 | |
| =X5 | 5 | 1101 | Y=y+C(X5)0...17 | |
| =X6 | 6 | 1110 | Y=y+C(X6)0...17 | |
| =X7 | 7 | 1111 | Y=y+C(X7)0...17 | |
| =AR0..17 | AU | 0001 | Y=y+C(AR)0...17 | |
| =AR18..35 | AL | 0101 | Y=y+C(AR)18...35 | |
| =QR0..17 | QU | 0010 | Y=y+C(QR)0...17 | |
| =QR18..35 | QL | 0110 | Y=y+C(QR)18...35 | |
| =IC0..17 | IC | 0100 | Y=y+C(IC)0...17 | |
| =IR0..17 | DU | 0011 | C(Y)0...17=y | |
| =IR0..17 | DL | 0111 | C(Y)18...35=y | |
| =None | Blank or N | 0000 | Y =y | |
| =Any symbolic index register | Any defined symbol* | |||
* Symbol must be defined as one of the index registers X0-X7 by use of an applicable pseudo-operation. (See discussion of EQU and POOL).
The examples following show how R-type modification variations are entered in the variable field and their resultant control effects upon Processor development of effective addresses.
| LOCATION | OPERATION (ADDRESS, TAG) | VARIABLE FIELD | COMMENTS | ||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| MODIFICATION TYPE | EFFECTIVE ADDRESS | ||||||||||||||||||||||
| 1. | B,0 | (R) | Y=B+C(X0)0...17 | ||||||||||||||||||||
| 2. | C,AL | (R) | Y=C+C(AR)18..35 | ||||||||||||||||||||
| 3. | M,QU | (R) | Y=M+C(QR)0..17 | ||||||||||||||||||||
| 4. | -2,IC | (R) | Y=C(IC)-2 | ||||||||||||||||||||
| 5. | *,DU | (R) | Operand0..17=IC | ||||||||||||||||||||
| 6. | 1,7 | (R) | Y=1+C(X7) | ||||||||||||||||||||
| 7. | 2,DL | (R) | Operand| 8. | B | (R) | Y=B
| 9. | B,N | (R) | Y=B
| 10. | C,ALPHA | (R) | Y=C+C(X2)
| | ||||||||
ALPHA EQU 2
Register then Indirect address modification in the GE-625/635 is a combination type in which both indexing (register modification) and indirect addressing are performed. For indexing modification under RI, the mnemonic substitutions for R are the same as those given under the discussion of Register (R) modification with the exception that DU or DL cannot be substituted for R. For indirect addressing (I), the Processor treats the contents of the operand address associated with the original instruction or with an indirect word as described on page III-14.
Under RI modification, the effective address Y is found by first performing the specified Register modification on the operand address of the instruction; the result of this R modification under RI obtains the address of an indirect word which is then retrieved.
After the indirect word has been accessed from memory and decoded, the Processor carries out the address modification specified by this indirect word. If the indirect word specifies RI, IR, or IT modification (any type specifying indirection), the indirect sequence is continued. When an indirect word is found that specifies R modification, the Processor performs R modification, using the register specified by the td field of this last encountered indirect word and the address field of the same word, to form the effective address Y.
It should be observed again that the variations DU and DL of Register modification (R) cannot be used with Register then Indirect modification (RI).
If the programmer desires to reference an indirect word from the instruction itself without including Register modification, he specifies the "no modifications" variation; under RI modification, this is indicated on the coding form by an asterisk alone placed in the variable field tag position.
The examples below illustrate the use of R combined with RI modification, including the use of (R) = N (no register modification). The asterisk (*) appearing in the modifier subfield is the Assembler symbol for I (Indirect). The address subfield, single-symbol expressions shown are not intended as realistic coding examples but rather to show the relation between operand addresses, indirect addressing, and register modification.
| LOCATION | OPERATION (ADDRESS, TAG) | VARIABLE FIELD | COMMENTS | ||
|---|---|---|---|---|---|
| MODIFICATION TYPE | EFFECTIVE ADDRESS | ||||
| 1. | Z+C(AR)0...17 | - - - - | Z,AU* B,1 | (R)* (R) | Y=B+C(X1)0...17 |
| 2. | Z | - - - - | Z,* B,QU | (R)* (R) | Y=B+C(QR)0..17 |
| 3. | Z B+C(X5)0...17 C+C(X3)0...17 | - - - - - - - - | Z,* B,5* C,3* M | (R)* (R)* (R)* (R) | Y=M |
Indirect then Register address modification is a combination type in which both indirect addressing and indexing (register modification) are performed. IR modification is not a simple inverse type of RI; several important differences exist.
Under IR modification, the Processor first fetches an indirect word (obtained via I or IR) from the core storage location specified by the address field y of the machine instruction; and the C(R) of IR are safe-stored for use in making the final index modification to develop Y.
Next, the address modification, if any, specified by this first indirect word is carried out. If this modification is again IR, another indirect word is retrieved from storage immediately; and the new C(R) are safe-stored, replacing the previously safe-stored C(R). If an IR loop develops, the above process continues, each new R replacing the previously safe-stored R, until something other than IR is encountered in the indirect sequence -- R, IR, or RI.
If the indirect sequence produces an RI indirect word, the R-type modification is performed immediately to form another address; but the I of this RI treats the contents of the address as an indirect word. The chain then continues with the R of the last IR still safe-stored, awaiting final use. At this point the new indirect word might specify IR-type modification, possibly re-newing the IR loop noted above; or it might initiate an RI loop. In the latter case, when this loop is broken, the remaining modification types are R or IT.
When either R or IT is encountered, it is treated as type R where R is the last safe-stored C(R) of an IR modification. At this point the safe-stored C(R) are combined with the y of the indirect word that produced R or IT, and the effective address Y is developed.
If an indirect modification without Register modification is desired, the no-modification variation (N) of Register modification should be specified in the instruction. This normally will be entered on the coding sheet as *N in the modifier part of the variable field. (The entry * alone is equivalent to N* under RI modification and must be used in this way.) The mnemonic substitutions for (R) are listed under the Register modification description.
The examples below illustrate the use of IR-type modification, intermixed with R and RI types, under the several conditions noted above.
| LOCATION | OPERATION (ADDRESS, TAG) | VARIABLE FIELD | COMMENTS | ||
|---|---|---|---|---|---|
| MODIFICATION TYPE | EFFECTIVE ADDRESS | ||||
| 1. | - - | Z,*QL | *(R) | ||
| Y=M+C(QA)18...35 | |||||
| Z | - - | M | (R) | ||
| 2. | - - | Z,*3 | *(R) | Y=C+C(X3)0...17 | |
| Z | - - | B,5* | (R)* | ||
| B+C(X5)0...17 | - - | C,IC | (R) | ||
| 3. | - - | Z,*3 | *(R) | Y=M+C(QR)0...17 | |
| Z | - - | B,5* | (R)* | ||
| B | - - | C,*QU | *(R) | ||
| C | - - | M,7 | (R) | ||
| 4. | - - | Z,DL | *(R) | C(Y)18...35-M | |
| Z | - - | B,3* | (R)* | ||
| B+C(X3)0...17 | - - | M,QL | *(R) | ||
Summary. Indirect then Tally address modification in the GE-625/635 is a combination type in which both indirect addressing and indexing (register modification) are performed. In addition automatic incrementing/decrementing of fields in the indirect word are done as hardware features, thus relieving the programmer of these responsibilities. The automatic tallying and other functions of the IT type modification greatly enhance the processing of tabular data in memory, provide the means for working upon character data, and allow termination on programmer-selectable numerical tally conditions. These features are explained in the nine subparagraphs to follow. (Refer to page 111-61 for the special word formats TALLY, TALLYD, and TALLYC for Assembler coding of the indirect words used with IT.)
The ten variations under IT modification are summarized in the following table. It should be noted that the mnemonic substitution for IT on the Macro Assembler coding sheet is simply (T); the designator I for indirect addressing in IT is not represented. (Note that one of the substitutions for T is I.)
| NAME OF THE VARIATION | CODING FORM SUBSTITUTION FOR I(T) | BINARY FORM (td FIELD) | EFFECT UPON THE INDIRECT WORD |
|---|
BINARY NAME OF THE CODING FORM FORM EFFECT UPON THE VARIATION SUBSTITUTION FOR I(T) (td FIELD) INDIRECT WORD Indirect I 1001 None. Increment address, ID 1110 Add one to the address; Decrement tally subtract one from the tally. Decrement address, DI 1100 Subtract one from the ad- Increment tally dress; add one to the tally. Sequence Character SC 1010 Add one to the character position number; subtract one from the tally; add one to the address when the character count crosses a word boundary. Character from Indirect CI 1000 None. Add Delta AD 1011 Add an increment to the address; decrement the tally by one. Subtract Delta SD 0100 Subtract an increment from the address;increase the tally by one. Fault F 0000 None; the Processor is forced to a fault trap starting at a predetermined, fixed location Increment address IDC 1111 Same as II) variation Decrement tally, except that further address and Continue modification can be performed. I Decrement address, DIG 1101 Same as DI except that Increment tally, further address modifica- and Continue tion can be performed.
Indirect (T) = I Variation. The Indirect (I) variation of IT modification is in effect a subset of the ID and DI variations described below in that all three -- I, ID, and DI -- make use of one in-direct word in order to reference the operand. The I variation is functionally unique, however, in that the indirect word referenced by the program instruction remains unaltered -- no incrementing/decrementing of the address field. Since the tm and td subfields of the indirect word under I are not interrogated, this word will always terminate the indirect chain.
The following differences in the coding and effects of *, *N, and I should be observed:
In the ID variation the effective address is the address field of the indirect word obtained via the tentative operand address of the instruction or preceding indirect word, whichever specified the ID variation. Each time such a reference is made to the indirect word, the address field of the indirect word is incremented by one; the tally portion of the indirect word is decremented by one. The incrementing and decrementing are done after the effective address is provided for theinstruction operation. When the tally reaches zero, the Tally Runout indicator is set.
The example following shows the effect of ID.
COMMENTS VARIABLE FIELD MODIFICATION EFFECTIVE LOCATION OPERATION ADDRESS, TAG TYPE ADDRESS REFERENCE Z,ID (T) B 1 Z B B+1 2
Assuming an initial tally of j, the tally runout indicator is B+n n+1 set on the jth reference.
In the DI variation the effective address is the address field minus one of the indirect word obtained via the tentative operand address of the instruction or preceding indirect word, whichever one specified the DI variation. Each time a reference is made to the indirect word, the address field of the indirect word is decremented by one; and the tally portion is incremented by one. The incrementing and decrementing is done prior to providing the effective address for the current instruction operation.
The effect of DI when writing programs is shown in ,the example following.
COMMENTS VARIABLE FIELD MODIFICATION EFFECTIVE LOCATION OPERATION ADDRESS, TAG TYPE ADDRESS REFERENCE - - Z,DI (T) B-i 1 Z -- B B-2 2
Assuming an initial tally of 4096-j the tally runout is B-n n set on the jth reference.
Characters are operated on in sequence from left to right within the machine word. The character position field of the indirect word is used to specify the character to be involved in the operation and is intended for use only with those operations that involve the A- or Q-registers. The tally runout indicator is set when the tally field of the indirect word reaches 0.
The tally field of the indirect word is used to count the number of times a reference is made to a character. Each time an SC reference is made to the indirect word, the tally is decremented by one; and the character position is incremented by one to specify the next character position. When character position 5 is incremented, it is changed to position 0; and the address field of the indirect word is incremented by one. All incrementing and decrementing is done after the effective address has been provided for the correct instruction execution.
The effect of SC is shown in the following example.
COMMENTS VARIABLE FIELD MODIFICATION EFFECTIVE LOCATION OPERATION ADDRESS, TAG TYPE ADDRESS REFERENCE Effective Character Address Position Reference z,SC (T) B 0 1 Z -- B B 1 2 B 5 6
An initial character position of 0 is assumed here. B+1 0 `7 Assuming an initial tally of j, the tally runout indicator is set on the jth reference. B+n 0 6n+1
For this variation substitution, the effective address is the address field of the CT indirect word obtained via the tentative operand address of the instruction or preceding indirect word that specified the CI variation. The character position field of the indirect word is used to specify the character to be involved in the operation and is intended for use only with the operations that involve the A- or Q-register.
This variation is similar to the SC variation except that no incrementing or decrementing of the address or character position is performed.
A CI example is:
COMMENTS VARIABLE FIELD MODIFICATION EFFECTIVE LOCATION OPERATION ADDRESS, TAG TYPE ADDRESS REFERENCE -- Z,CI (T) Y=B Z -- B
Each time such a reference is made to the indirect word, the address field of the indirect word is increased by delta and the tally portion of the indirect word is decremented by one. The addition of delta and decrementing is done after the effective address is provided for the instruction operation.
The example following shows the effect of AD.
COMMENTS VARIABLE FIELD MODIFICATION EFFECTIVE LOCATION OPERATION ADDRESS, TAG TYPE ADDRESS REFERENCE -- Z,AD (T) B 1 Z B (R) 2 B+2d 3 Bvn6
The address and tally fields are used as described under the ID variation. The tag field uses the set of GE-625/635 instruction address modification variations under the following restrictions: No variation is permitted which requires an indexing modification in the IDC cycle since the indexing adder is in use by the tally phase of the operation. Thus, permissible variations are any form of I(T) or I(R); but if (R)I or (R) is used, R must equal N.
The effect of IDC is indicated in the following example:
COMMENTS VARIABLE FIELD MODIFICATION EFFECTIVE LOCATION OPERATION ADDRESS, TAG TYPE ADDRESS REFERENCE Effective Character Address Position Z,IDC (T) B 1 Z B (R) B+1 2
Assuming an initial tally of j, the tally runout indicator Bñn nñ 1 is set on the jth reference.
COMMENTS VARIABLE FIELD MODIFICATION EFFECTIVE LOCATION OPERATION ADDRESS, TAG TYPE ADDRESS REFERENCE - - Z, DIG (T) Z B,*3 *(R) C+C(X3) 1 B1 - - C,QU (R) A+C(X3) 2 B-2 - - M,5* (R)* Q+C(AR)0-17 3 B-3 - - D, *AU *(R) p M+C(X5)0..1rjr - A (R) D - - Q (R)
Assuming an initial tally of 4096-j, the tally runout indicator is set on the jth reference.
Pseudo-operations are so-called because of their similarity to machine operations in an object program. In general, however, machine operations are produced by computer instructions and perform some task, or part of a task, directly concerned with solving the problem at hand. Pseudo-operations work indirectly on the problem by performing machine conditioning functions, such as memory allocating, and by directing the Macro Assembler in the preparation of machine coding. A pseudo-operation affecting the Assembler may generate several, one, or no words in the object program.
All pseudo-operations for the Macro Assembler are grouped according to function and described (in this Chapter) as to composition and use. The pseudo-operation functional groups and their uses are:
| FUNCTIONAL GROUP | PRINCIPAL USES
| Control pseudo-operations
| Selection of printout options for the assembly listing, direction of
punchout of absolute/relocatable binary program decks, selection of
format for the absolute binary deck.
| Location counter pseudo-operations
| Programmer control of single or multiple instruction counters.
| Symbol defining pseudo-operations.
| Definition of Assembler source program symbols by means other than
appearance in the location field of the coding form
| Data generating pseudo-operations
| Production of binary data words for the assembly program.
| Storage allocation pseudo-operations
| Provision of programmer control for the use of memory.
| Special pseudo-operations
| Generation of zero operation code instructions, of binary words
divided into two 18-bit fields, and of continued subfields for selected
pseudo-operations.
| MACRO pseudo-operations
| Begin and end MACRO prototypes; Assembler generation of MACRO-argument
symbols; and repeated substitution of arguments within MACRO prototypes.
| Conditional pseudo-operations
| Conditional assembly of variable numbers of input words based upon the
subfield entries of these pseudo-operations.
| Program linkage pseudo-operations
| Generation of standard system subroutine calling sequences and return
(exit) linkages
| Address,tally pseudo-operations
| Control of automatic address, tally, and character
incrementing/decrementing.
| Repeat mode coding formats
| Control of the repeat mode of instruction execution (coding of RPT,
RPD, and RPL instructions)
| |
|---|
The above pseudo-operation functional groups, together with their pseudo-operations, are given as a complete listing with page references in Appendix D.
The subset of the control pseudo-operations consisting of those operations which may best be described as switches (which current state may be `on' or `off') are comprised of the following:
DETAIL, PCC, REF, PMC, INHIB, PUNCH, EDITP
The description of the variable field is common to all of these and the CRSM pseudo-operation discussed under Macro pseudo-operations.
Provisions have been made to allow the user to treat these switches in a push-down pull-up manner so that he may recall prior states of a switch and retrieve that state at some later point. The depth to which this may be accomplished is 35; a switch may therefore have a current state plus 35 "remembered" states.
The mnemonic representing the push-down feature is SAVE; pull-up or retrieve prior is designated by the mnemonic RESTORE. The mnemonic for turning the current state of a switch on is ON; its counterpart is OFF. If a switch alteration is implied but not explicitly given, its current state will be alternated (i.e., if off, turn on); if alteration is not implied, its current state will be unchanged changed (see example 4 below).
The eight possible variable field representations are:
| 1. | CRSM* | ON | (turn switch on) |
| 2. | CRSM* | OFF | (turn switch off) |
| 3. | CRSM* | (alternate current status of switch) | |
| 4. | CRSM* | SAVE | (push down--remember current state and leave unchanged) |
| 5. | CRSM* | SAVE, ON | (push down, and set switch on) |
| 6. | CRSM* | SAVE, OFF | (push down, and set switch off) |
| 7. | CRSM* SAVE, | (push down, and alternate current switch setting) | |
| 8. | CRSM* RESTORE | (pull up prior state of switch) |
The Assembler has been preset with a `current' state for each switch, and 35 remembered states which are the same. Restores past this point will pull up an ON state for all switches. The initial setting is given in the discussion of each of the pseudo operations in question, and corresponds to normal mode of operation.
*CRSM is used for illustrative purposes only
DETAIL ON/OFF (Detail Output Listing)
Some pseudo-operations generate no binary words; however, several of them generate more than one. The generative pseudo-operations are: OCT, DEC, BCI, DUP, CALL, SAVE, RETURN, ERLK, LIT, and VFD. The DETAIL pseudo-operation provides control over the amount of listing detail generated by the generative pseudo-operations.
The use of the DETAIL OFF pseudo-operation causes the assembly listing to be abbreviated by eliminating all but the first word generated by any of the above pseudo-operations. In the case of the DUP pseudo-operation, only the first iteration will be listed. The DETAIL ON pseudo-operation causes the Assembler to resume the listing which had been suspended by a DETAIL OFF pseudo-operation.
If at the end of the listing the Assembler is in the DETAIL OFF mode, the literal pool will not be printed, but a notation will be made as to its presence.
If the Assembler is already in a specified ON/OFF mode, then the pseudo-operation requesting the same ON/OFF mode is ignored.
NAME ON/OFF (Control Output Listing)
The use of LIST in the operation field with OFF in the variable field causes the normal listing to change as follows: the instruction LISTOFF will appear in the listing; thereafter, only instructions which are flagged in error will appear. If the assembly ends in the LIST OFF mode, only the error messages will appear.
The use of LIST in the operation field with ON in the variable field causes the normal listing, which was suspended by a LIST OFF pseudo-operation, to be resumed. If the Assembler is already in a specified ON/OFF mode, then the pseudo-operation requesting the same ON/OFF mode is ignored.
PCC ON/OFF (Print Control Cards)
The PCC pseudo-operation affects the listing of the following pseudo-operations:
| DETAIL | LIST | TTL | PMC |
| EJECT | PCC | TTLS | PUNCH |
| LBL | REF | CRSM | IDRP |
| INE | IFE | IFO | TFL |
PCC ON causes the affected pseudo-operations to be printed. PCC OFF causes the affected pseudo-operations to be suppressed; this is the normal mode at the beginning of the assembly. If the Assembler is already in a specified ON/OFF mode, then the pseudo-operation requesting the same ON/OFF mode is ignored.
The REF pseudo-operation controls the Assembler in making entries in the symbol reference table.
REF ON causes the Assembler to begin making entries into the symbol reference table. REF OFF causes the Assembler to suppress making entries into the symbol reference table.
If the Assembler is already in a specified ON/OFF mode, then the pseudo-operation requesting the same ON/OFF mode is ignored.
PMC ON/OFF (Print MACRO Expansion)
The PMC pseudo-operation causes the Assembler to list or suppress all instructions generated by a MACRO call.
PMC ON causes the Assembler to print all generated instructions. PMC OFF causes the Assembler to suppress all but the MACRO call.
If the Assembler is already in a specified ON/OFF mode, then the pseudo-operation requesting the same ON/OFF mode is ignored.
INHIB ON/OFF (Inhibit Interrupts)
The instruction INHIB ON causes the Assembler to set the program interrupt inhibit bit in bit position 28 of all machine instructions which follow the pseudo-operation. The setting of the instruction interrupt inhibit bit continues for the remainder of the assembly, unless the pseudo-operation INHIB OFF is encountered.
The INHIB OFF causes the Assembler to stop setting the inhibit bit in each instruction, if used when the Assembler is in the INHIB ON mode.
If the Assembler is already in a specified ON/OFF mode, then the pseudo-operation requesting the same ON/OFF mode is ignored.
< a name="PUNCH">PUNCH ON/OFF (Control Card Output)
Subject to the DECK/NDECK option of the OMAP call carcl, the normal mode of the Assembler is to punch binary cards for everything it assembles. If PUNCH is used in the operation field with OFF in the variable field, the binary deck will not be punched, beginning at the point the Assembler encounters the pseudo-operation.
These conventions hold true for both the output binary deck, and the load file counterpart, in the case of assemble and execute activities.
If the Assembler is already in a specified ON/OFF mode, then the pseudo-operation requesting the same ON/OFF mode is ignored.
EDITP (Edit Print Lines)
This pseudo-operation has a special application. It is for the program which includes the character ? (17) and/or ! (77) punched somewhere on a symbolic card. In normal operation these characters have special meaning to the printer subsystem and may cause character shifting, line suppression, slewing, or buffer overflow. As such, an EDTTP ON instruction, causes the output routine to issue printer commands which will treat these as non-special characters. The Assembler will then remain in this mode until an EDTTP OFF instruction is encountered.
EJECT (Restore Output Listing)
The EJECT pseudo-operation causes the Assembler to position the printer paper at the top of the next page, to print the title(s), and then print the next line of output on the second line below the title(s).
REM (Remarks)
The REM pseudo-operation causes the contents of this line of coding to be printed on the assembly listing (just as the comments appear on the coding sheet). However, for purposes of neatness, columns 8-10 are replaced by blanks before printing.
REM is provided for the convenience of the programmer; it has no other effect upon the assembly.
* (In Column One--Remarks)
A card containing an asterisk (*) in column 1 is taken as a remark card. The contents of columns 2-80 are printed on the assembly listing (just as they appear on the coding sheet); the asterisk has no other effect on the assembly program.
LBLLBL (Label)
LBL causes the Assembler to serialize the binary cards using columns 73-80, except when punching full binary cards by use of the FUL pseudo-operation. The LBL pseudo-operation allows the programmer to specify a left-justified alphabetic label for the identification field and begin serialization with some initial serial number other than zero. The LBL pseudo-operation also allows the programmer to specify up to 42 characters of comments on the $ OBJECT card of the binary deck. The comment, if present, begins in column 16 of the $ OBJECT card. The following conditions apply:
TTL (Title)
The TTL pseudo-operation causes the printing of a title at the top of each page of the assembly listing. In addition, when the Assembler encounters a TTL card, it will cause the output 1isting to be restored to the top of the next page and the new title will be printed. The information punched in columns 16-72 is interpreted as the title.
Redefining the title by repeated TTL pseudo-operations may be used as often as the programmer desires. Deletion of the title may be accomplished by a TTL, pseudo-operation with a blank varialle field. If a decimal integer appears in the location field, the page count will be renumbered beginning with the specified integer.
The TTLS pseudo-operation is identical in function to the TTL pseudo-operation except that it causes subtitling to occur. When a TTLS pseudo-operation is encountered, the subtilie provided in columns 16-72 replaces the current subtitle; the output listing is restored to the top of the next page. The title and new subtitle are then printed.
The bmaximum number of subtitles that may follow a title is one.
ABS (Output Absolute Text)
The ABS pseudo-operation causes the Assembler to output absolute binary text.
The normal mode of the Assembler is relocatable; however, if absolute text is required for a given assembly, the ABS pseudo-operation should appear in the deck before any instructions or data. It may be preceded only by listing pseudo-operations. It may, however, appear repeatedly in an assembly interspersed with the FUL pseudo-operation. `It should be noted that the pseudo-operations affecting relocation are considered errors in an absolute assembly.
Those pseudo-operations that will be in error if used in an absolute assembly are: BLOCK SYMDEF ERLK SYMREF
(Refer to the descriptions of binary punched cardfprmats in this chapter for details of the absolute binary text.)
REF ON/OFF (References)
LBL (Label)
TTLS (Subtitle)